Answer the question
In order to leave comments, you need to log in
Access-list does not work. What's wrong?
Access-list does not work on the outgoing interface , the
system is very simple cisco router for example 3725 (c3725-adventerprisek9-mz.124-25d) is connected by the FastEthernet0/1 interface to any switch
router R1 configuration
interface Loopback0
ip address 192.168.2.1 255.255.255.255
!
interface Tunnel0
ip unnumbered Loopback0
ip ospf network point-to-point
ip ospf mtu-ignore
tunnel source FastEthernet0/1
tunnel destination 192.168.1.1
!
interface FastEthernet0/1
ip address 192.168.1.2 255.255.255.0
ip access-group 100 in
ip access-group 101 out
duplex auto
speed auto
no shutdown
!
router ospf 1
router-id 192.168.2.1
log-adjacency-changes
network 192.168.2.1 0.0.0.0 area 192.168.1.1
!
ip route 0.0.0.0 0.0.0.0 FastEthernet0/1
!
access-list 100 deny gre any any log
access-list 101 deny gre any any log
no cdp run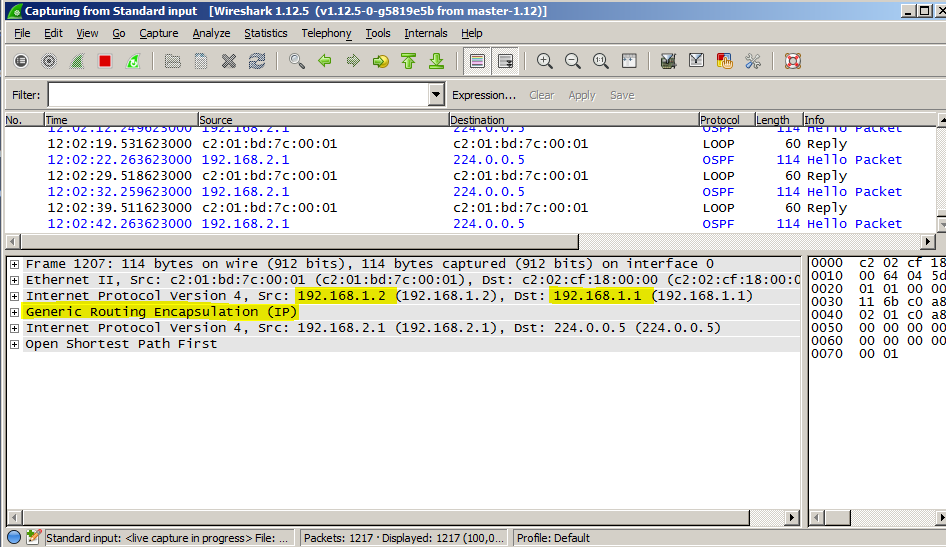
Answer the question
In order to leave comments, you need to log in
You are absolutely right. On IOS routers, traffic initiated by the router itself is not ACLed.
If there is such a critical need to keep traffic out, then the easiest option is to wrap targeted traffic on the loopback interface using a local route-map.
ip local policy route-map
yes, it seems to me once again the 2nd case
, I will read about it in more detail
I hope that I won’t say stupidity, but I’ll voice 2 of my versions that come to mind:
1) You can’t hang more than one ACL per interface / protocol / direction
2) ACL does not affect traffic generated by the router itself (your case)
Can be blocked at the control-plane policy level. In the current form, it will not work, because. traffic, the router's own traffic will not be filtered. But the incoming tunnel will still not rise, so the task is solved to some extent ..
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question