Answer the question
In order to leave comments, you need to log in
Will such a security system help?
Hello. I have all the security updates on the server, etc. But still, I'm afraid that if they get access to the database, they can do business (I have an online game. I got into the database, found myself and drew parameters for myself, and maybe my neighbors). I encrypt login and email using xxtea. The key is embedded in the source of the Golang project. There are only compiled binaries on the server. So without decompiling Go, you won't be able to find out your string.
That's what I have in the database 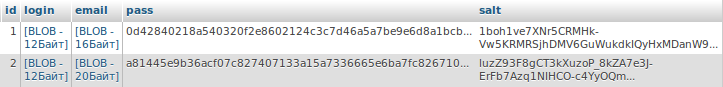
Or is it still a useless measure?
What else do you recommend?
Thank you all
UPD.
Doesn't affect performance. Encryption and decryption take 1 ms
pass and salt (sha512 + sha 256 + salt)
func userSave(result []string) bool {
//result[0] = login
//result[1] = email
//result[2] = pass
var salt string = newSalt()
if salt == "err" {
return false
}
var pass string = passwordHash(salt + result[2] + salt + result[1] + salt + result[1] + salt + result[2] + salt + result[0])
res, err := DB.Exec("INSERT INTO users (login, email, pass,salt)VALUES(?,?,?,?)", string(xxtea.Encrypt([]byte(v.Trim(result[0])), X_secret)), string(xxtea.Encrypt([]byte(v.Trim(result[1])), X_secret)), pass, salt)
if err != nil {
print(err)
return false
}
insertId, err := res.LastInsertId()
if err != nil {
print(err)
return false
}
print(insertId)
return true
}
func newSalt() string {
rb := make([]byte, 64)
_, err := rand.Read(rb)
if err != nil {
return "err"
}
return base64.URLEncoding.EncodeToString(rb)
}
func passwordHash(pass string) string {
text := v.Trim(pass)
hash := sha512.New()
hash.Write([]byte(text))
return1 := hex.EncodeToString(hash.Sum(nil))
var i int = 0
hashi := sha256.New()
for i <= 10 {
i = i + 1
hashi.Write([]byte(return1))
return1 = hex.EncodeToString(hashi.Sum(nil))
}
return return1
}Answer the question
In order to leave comments, you need to log in
So without decompiling Go, you won't be able to find out your string.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question