Answer the question
In order to leave comments, you need to log in
Why is reading not allowed?
Whole code:
#include <fstream>
#include <iostream>
#include <stdio.h>
#include <iomanip>
#include <windows.h>
using namespace std;
unsigned char b[] = "\xa1\x00\x70\xe8\x00";
int mySequency[256] = { 3 };
void *exec = VirtualAlloc(0, sizeof b, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
int main()
{
memcpy(exec, b, sizeof b);
((void(*)())exec)();
system("pause");
return 0;
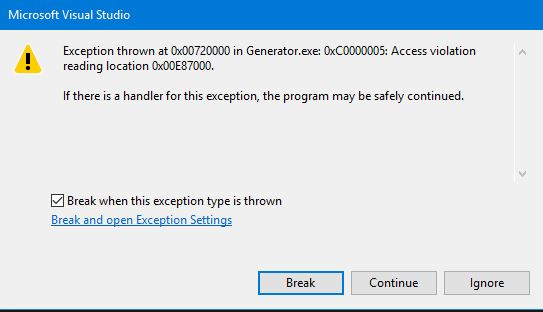
}
DWORD old_protect;
VirtualProtect((DWORD*)mySequency, 256, PAGE_READWRITE, &old_protect);mov eax, dword ptr[mySequency]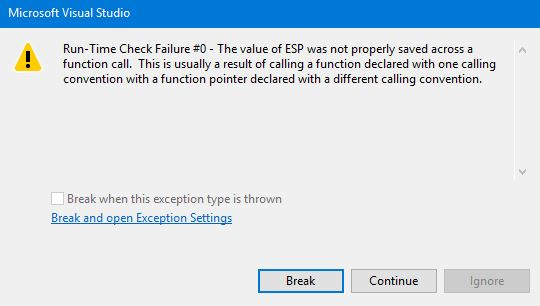
Answer the question
In order to leave comments, you need to log in
No, your opcode matches the instruction
. Who told you that the mySequency variable is located at 0xe87000? Each time you run the program, its address may be different.
Great, you've already run some code. But the challenge agreement did not survive.
1. Use the STDCALL calling convention. Then the function will have to clean up after itself. Since there are no local variables in it, no cleanup is required.
typedef uint32_t WINAPI (*SomeFunc)();
uint32_t result = (SomeFunc)exec();Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question