Answer the question
In order to leave comments, you need to log in
Why does the "Key Exchange" and "Cipher Strength" test at ssllabs.com pass 90?
I got a Let's Encrypt certificate, I want to achieve 100 points in all parameters, but I can't get through "Key Exchange" and "Cipher Strength", tell me why?
ssl_session_cache shared:le_nginx_SSL:10m;
ssl_session_timeout 1440m;
ssl_session_tickets off;
ssl_protocols TLSv1.3 TLSv1.2;
ssl_prefer_server_ciphers off;
ssl_ciphers "ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384";
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;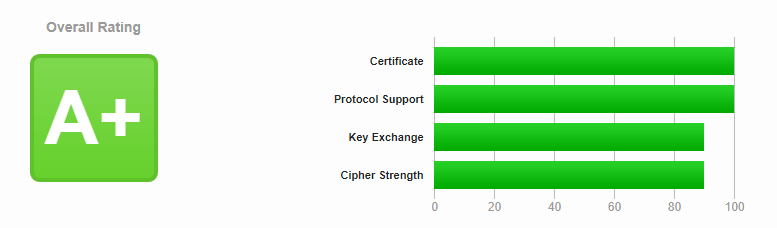
Answer the question
In order to leave comments, you need to log in
1.
For Cipher Strength 100, you need to get rid of "SHA256" in nginx:
instead of the ssl_ciphers line, you need three of these (fresh nginx, of course):
ssl_conf_command Ciphersuites TLS_AES_256_GCM_SHA384;
ssl_conf_command CipherString ECDHE-RSA-AES256-GCM-SHA384;
ssl_ciphers 'TLS_AES_256_GCM_SHA384:ECDHE-RSA-AES256-GCM-SHA384';Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question