Answer the question
In order to leave comments, you need to log in
Which of the log events is abnormal?
Someone remotely breaks my PC: there is an antivirus, it seems that all remote access services are disabled, nevertheless strange events appear, updates are downloaded, hive logs are cleared and in the end my file system was broken: it was not possible to restore from the access point, not to mention substitution of system executable files, including antivirus. None of the "specialists" wanted to see anything, but what is happening is what is in the pictures.
I'm going to contact the FSB, help me understand which of the events are malicious and how to find a vulnerable spot?
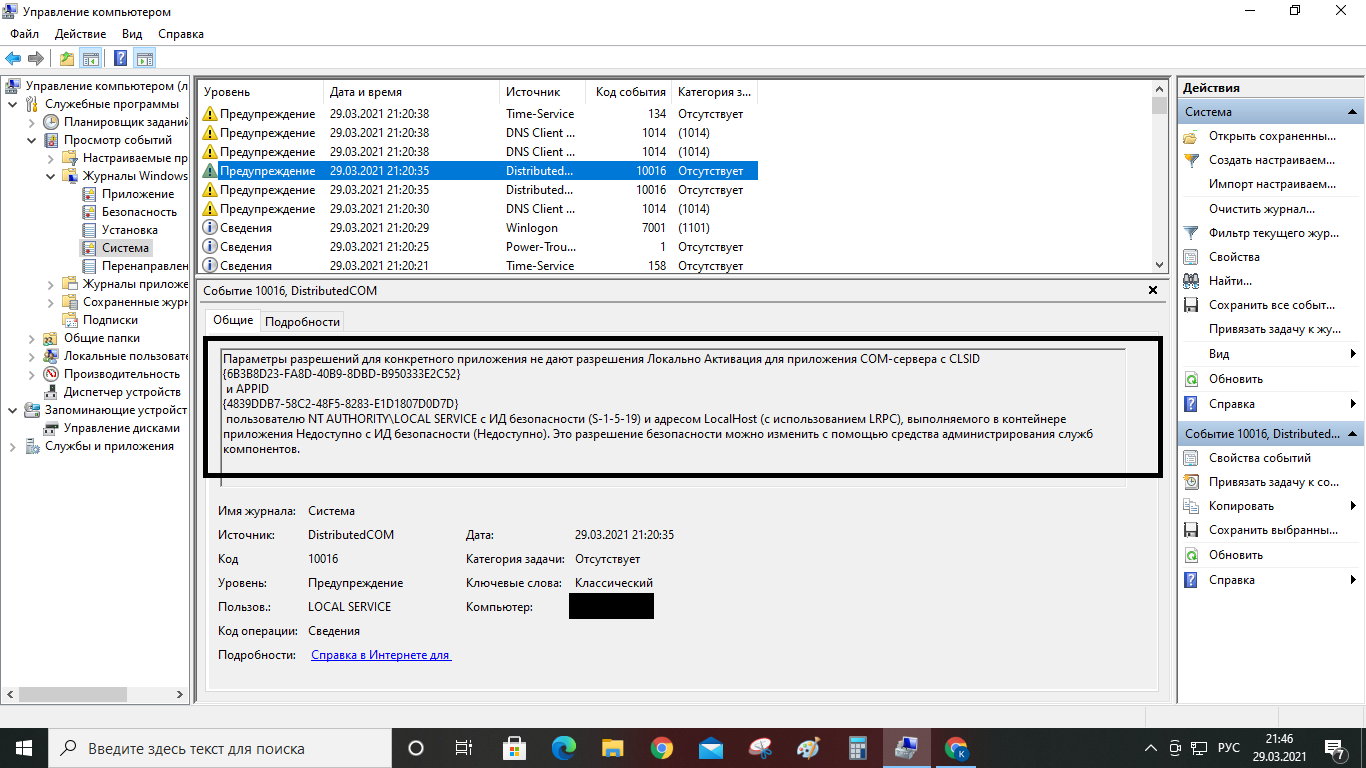
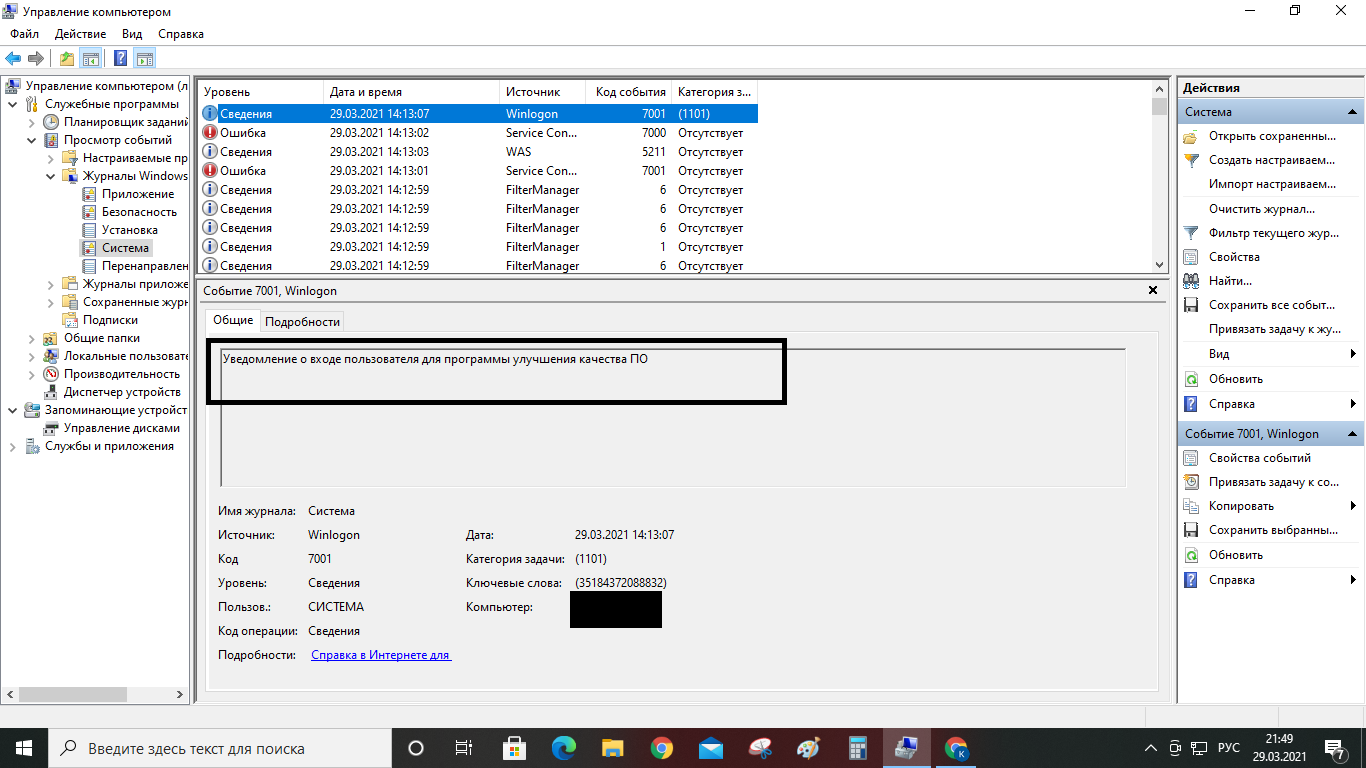
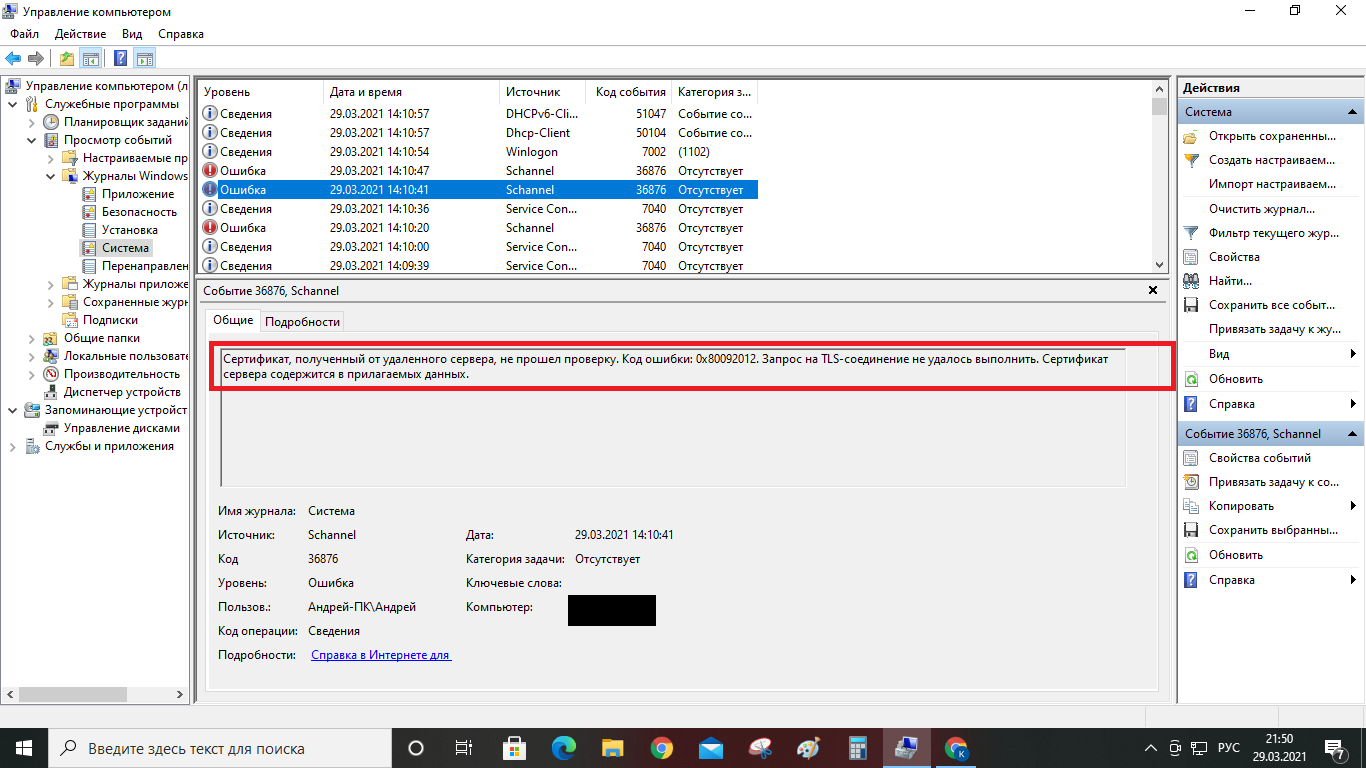
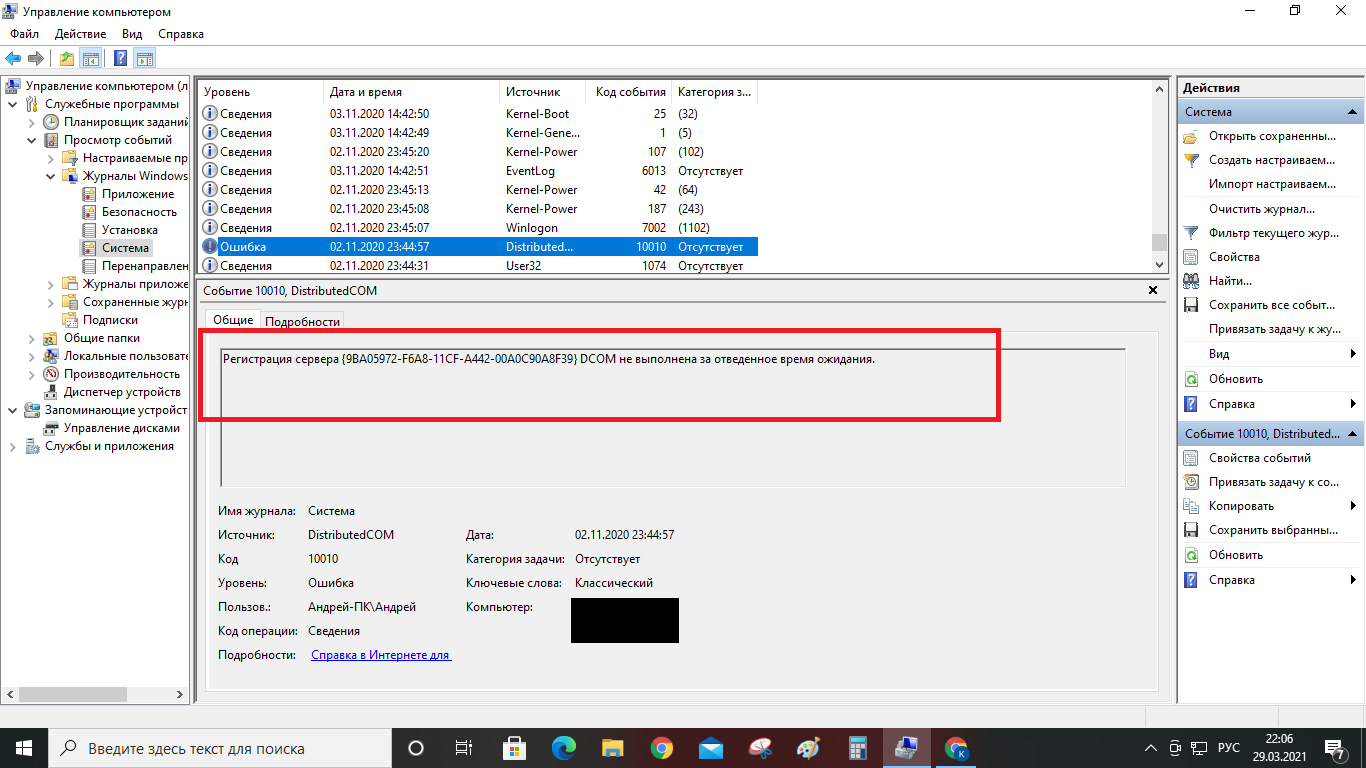
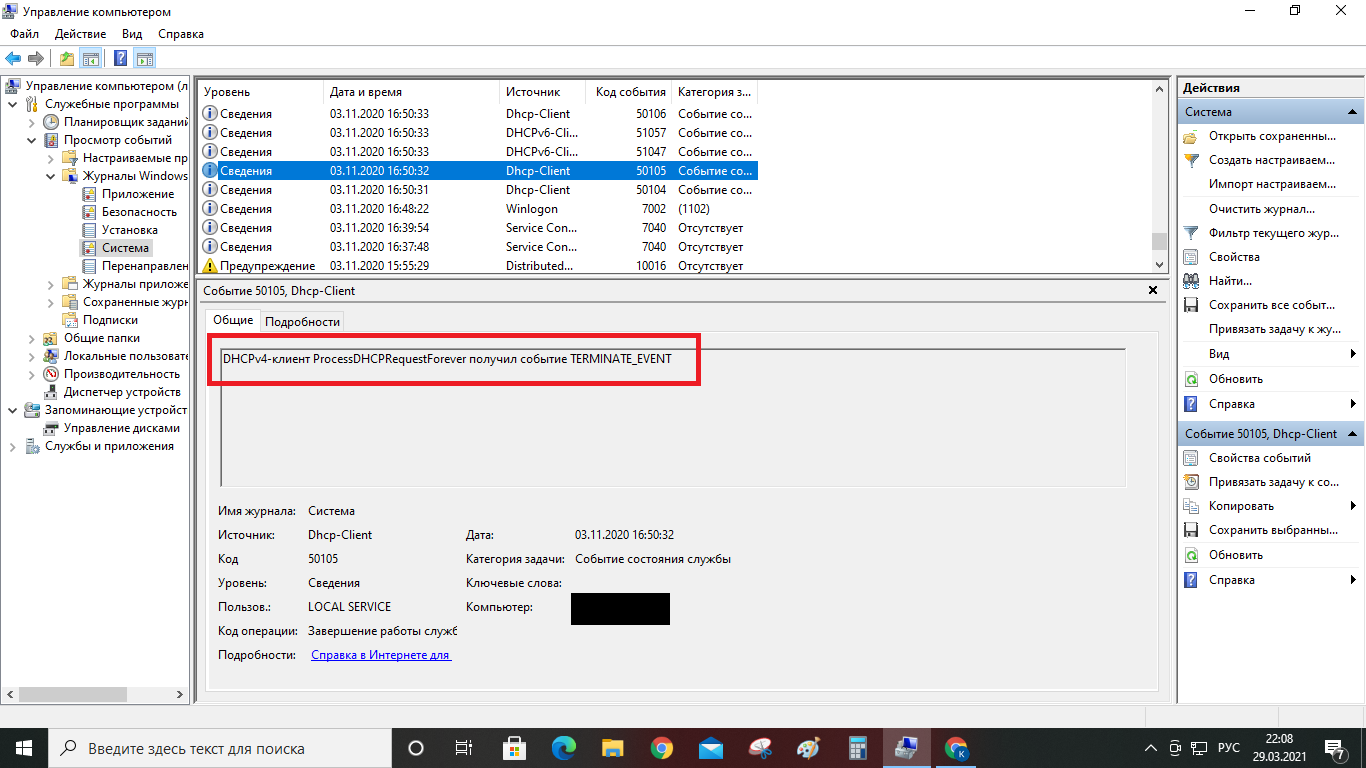
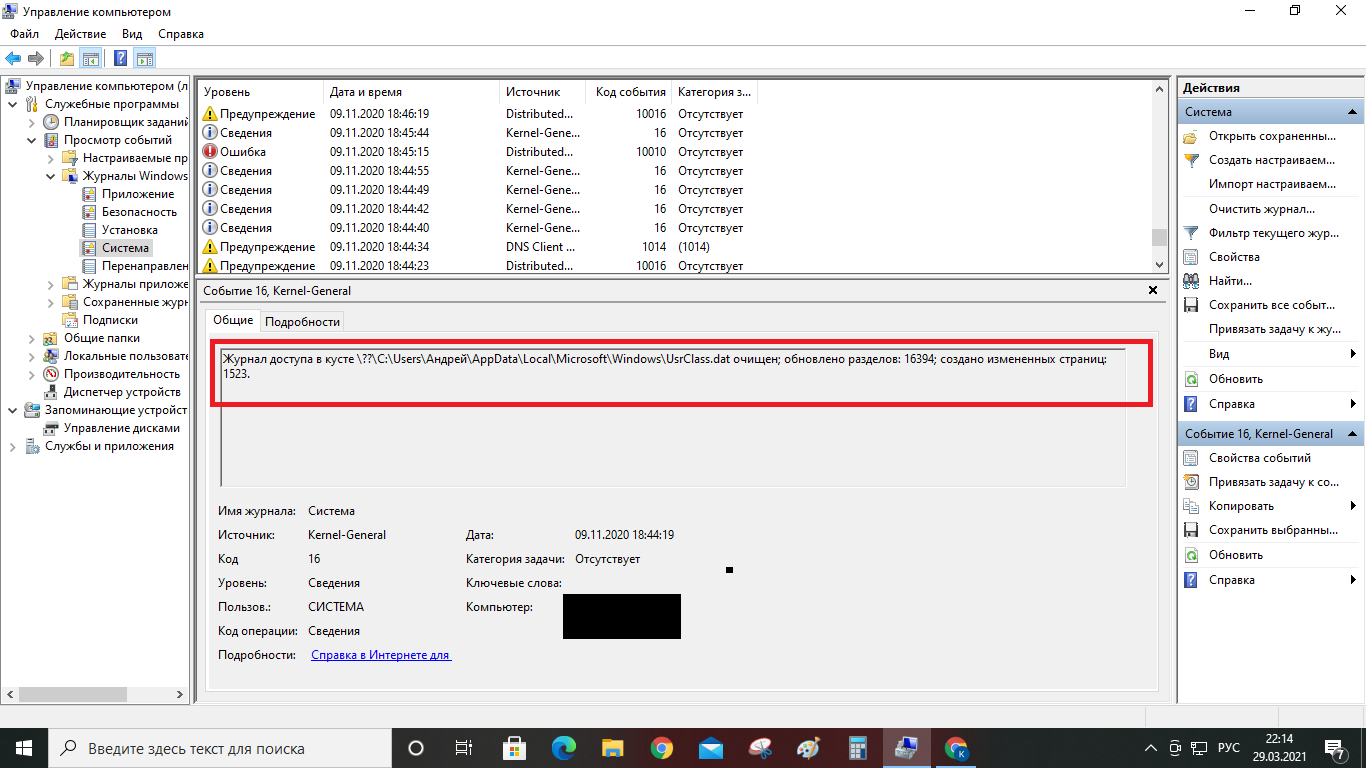
Answer the question
In order to leave comments, you need to log in
Horses, people mixed up in a bunch ...
You mixed everything in one question - and the FS broke, and the files were changed, and so on. The above pictures are typical for a regular PC under ten and even under seven, almost the same picture is often observed, even on computers that have never seen the Internet, let alone some kind of hack. There is no pathology here.
I want to know about these records - you just need to google, read the forums, and in the end you will come to the conclusion that there is nothing to dig there if there are no problems.
The FSB will simply ignore you. Don't be embarrassed. There is a problem - solve, but separately. And then it turns out that a half-dead computer, with a broken disk, or swollen capacitors in the PSU, and we are looking for hackers here.
You are now in the stage of accepting the inevitable "anger". Therefore, write nonsense about the FSB, empathy, etc.
You have lost some data and either you will restore it and pay money for it, or at some point, having gone through all the stages, you will accept their loss and move on with your life.
They will not be able to answer your question here - screenshots are not enough to at least understand something - you need a thoughtful study. I think no one will agree to do it here by correspondence.
So accept the loss of data, or ask the right questions - how can you recover them, etc. And in this case - you need to stop all attempts to do it yourself - if you do not want to lose them completely by your actions.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question