Answer the question
In order to leave comments, you need to log in
What configuration to choose to build a network?
Hello. Finally received the long-awaited equipment. Now I'm sitting scratching my head with the network configuration.
Initially, I planned like this:
The Mikrotik RB3011 router distributes the RTK provider. This router has IP 10.0.1.2
Devices with IP are connected to this router:
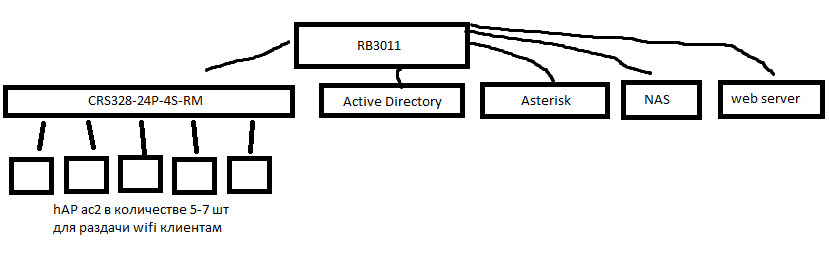
Answer the question
In order to leave comments, you need to log in
Usually, the network is still designed first, then the hardware is bought. You somehow turned out the other way around, it's strange.
It can be divided into classic zones - Ext, Int and DMZ
Ext includes what should not be available from the inside - for example, guest Wi-Fi
Int - what should not be accessible from the outside - for example, file storage and workstations. Business-critical workstations, such as accounting and the general director, fall into their own separate zone (Int-VIP)
The DMZ gets what should be accessible both from inside and outside - for example, a WWW server and Asterisk.
All these VLANs, firewalls and zones are needed so that in the event of an infection or an external attack, not all cars fly, but only some small fraction (the cryptolocker downloaded by the driver should not get to the station of the gender).
on necrotic and so it will do. otherwise a competent answer is more expensive than the long-awaited equipment that is not clear how to use it :)
broke once again from clay and sticks to make candy. bought - go for it!
push everyone into one net.
into a separate one - only the guest wifi
set up everything, including capsman, on the central router
Everything)
I would divide into subnets - separately management, separately working network and separately guest. Then unwind everything with vlans and configure routing between networks.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question