Answer the question
In order to leave comments, you need to log in
Static IP over L2 OpenVPN tunnel - what's missing and why doesn't it work?
Situation: there is a VPS with a white IP and there is a certain student project that lives deep in the campus network under two NATs, i.e. not accessible from the outside. 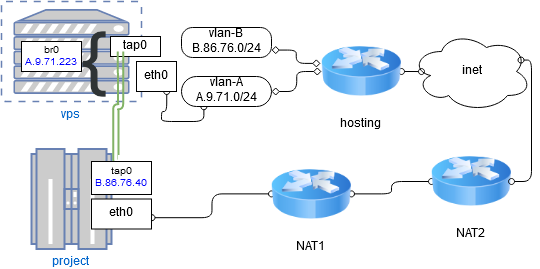
Task: the ability to access the project from the outside from the Internet (from home, for example).
General solution strategy: buy 2 more white IP addresses for VPS and forward at least one of them using OpenVPN to the project server.
Solution steps: Two white IP addresses from the IP1 and IP2 ranges are purchased. They are on the same /24 subnet, that is, apparently, the VPS was simply included in such a VLAN, where reserve addresses are found. IP Forwarding on VPS is enabled.
At first, I set up an OpenVPN tunnel in dev tun (l3) mode, assigning these white addresses to both ends of it. The tunnel itself worked, but the problem arose in the fact that in this VLAN, in which both of these addresses were sitting, the router constantly sent ARP who-has to both addresses (and others) and, of course, only that end could respond to such requests tunnel that was on the VPS itself. The second one could not, because ARP does not go through L3 tunnels, and without this, the router did not know the MAC and could not send IP packets to it.
All right... I lift the tunnel in the dev tap (L2) mode. Here is the server config
proto tcp4-server
bind XXX.9.71.223
cipher AES-256-CBC
dev tap
secret /etc/openvpn/static.keyproto tcp4-client
remote XXX.9.71.223
cipher AES-256-CBC
dev tap
secret /etc/openvpn/static.keyAnswer the question
In order to leave comments, you need to log in
I understood the question, but I didn’t master your decision,
I wouldn’t do tap at all and other br0
, everything can be simply routed
according to this scheme:
everything is solved by simple routing
on your server C, assign IP1 to the lo1 interface
sudo ip link add name lo1 type dummy , set
up an openvpn tunnel (B server, C client and do not forget to push "redirect-gateway def1" in the config)
on host B, specify a static route to IP1 to the tunnel
Next, ask the person who issued the IP1 address how it is routed to A.
if as a host route where next-hop points to host B, then everything should already work.
if it was just reserved for you in VLAN (link1) without a separate route, then there are two ways
Yes, it turned out beautifully. That is, after all, it turned out that it was possible to lift this entire structure to L3, and not L2.
I had to tweak your method a bit and it worked. It turns out that the static proxyARP is raised quite by the regular means of the OS, the cat might think.
First, there was no need to create dummy interfaces - I hung both white IPs on both ends of tun0/tun0.
Secondly, the static route on the server B OpenVPN prescribes itself, if you specify the p2p topology in its settings
. Thirdly, most likely, you will have to use redirect-gateway on the client side without def1, because there is also an interface with a local address, in which the change of the default gateway causes misunderstanding. I will experiment.
Thank you very much!
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question