Answer the question
In order to leave comments, you need to log in
Squid + Mikrotik how to configure correctly?
Hello.
Decided to put Squid to monitor who goes where.
The network diagram looks like this:
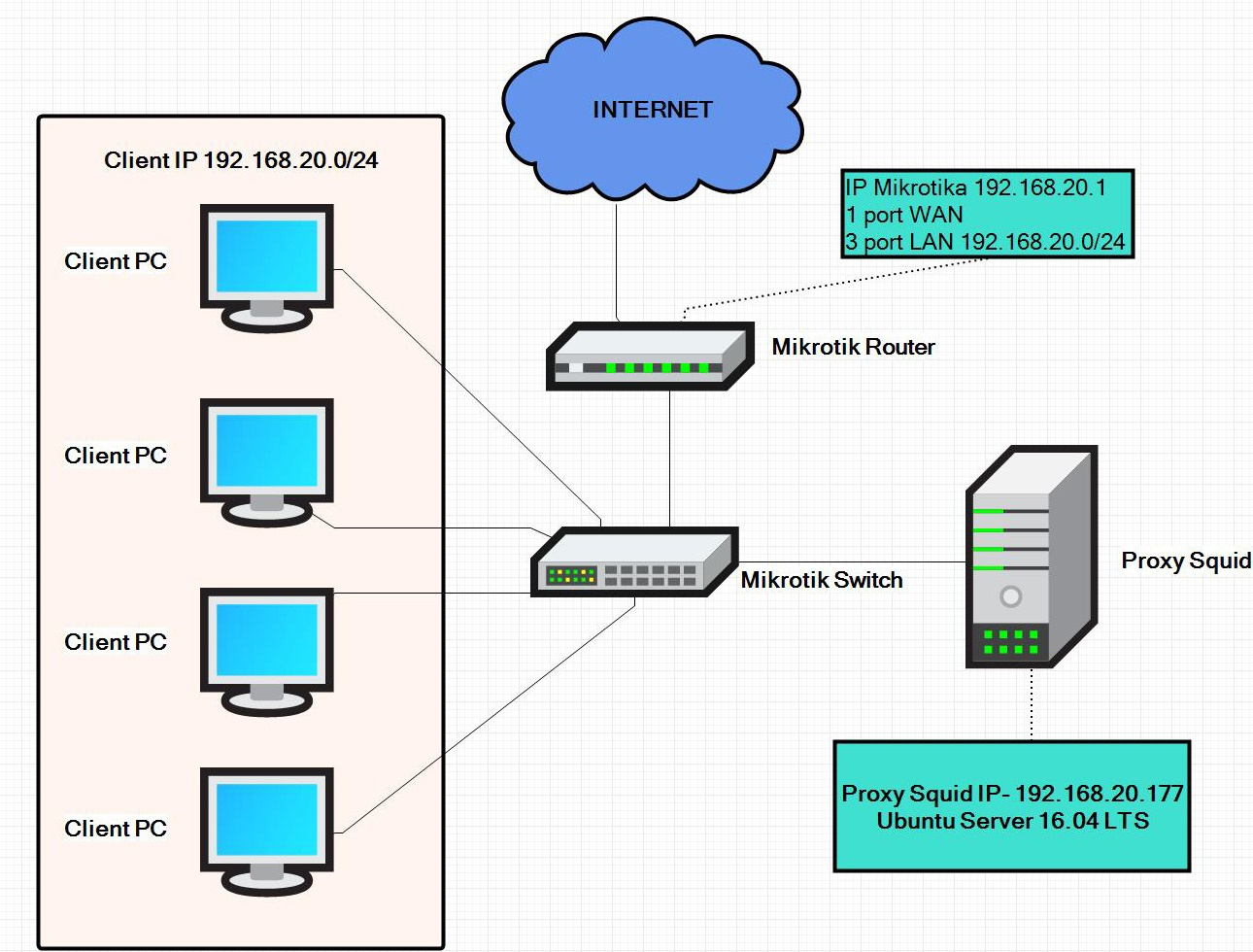
Something went wrong. Namely, when prerouting-a is enabled in Mikrotik, it sells the entire Internet
. Kanfik in Mikrotik
looks
like
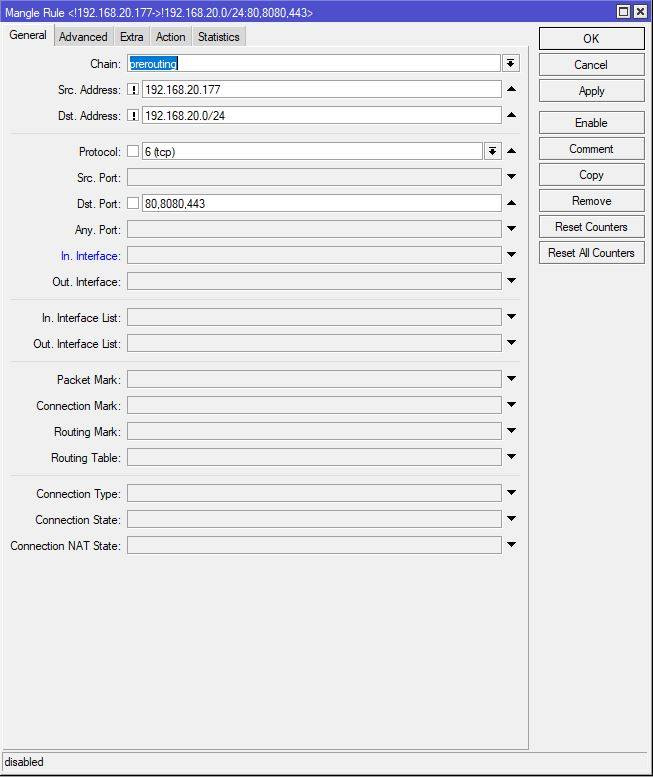
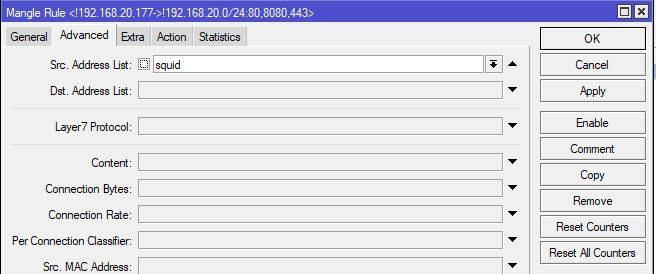
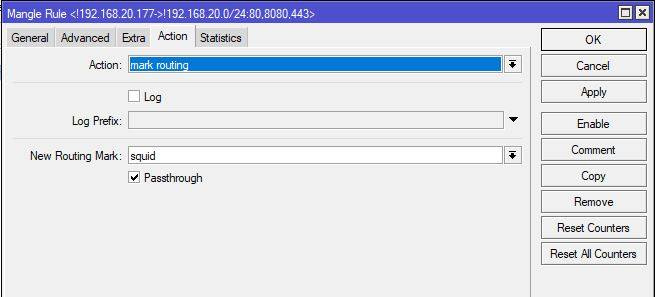
this ---------------
Now about Squid
I installed it on Ubuntu Server 16.04 LTS, everything is step by step using this article
Squid.config looks like this:
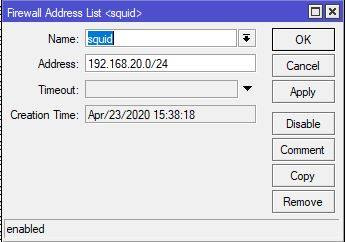
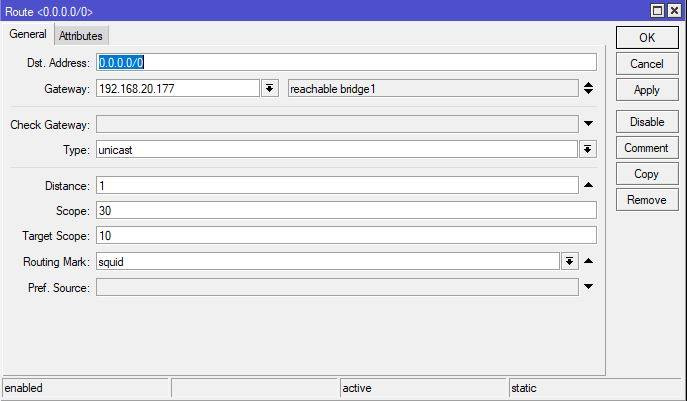
acl local src 192.168.20.0/24 # RFC1918 possible internal network
dns_nameservers 8.8.8.8
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_port 192.168.20.1:3130 options=NO_SSLv3:NO_SSLv2
http_port 192.168.20.1:3128 intercept=NO_SSLv3:NO_SSLv2
https_port 192.168.20.1:3129 intercept ssl-dump options=ALL:NO_SSLv3:NO_SSLv2 connection-auth=off cert=/etc/squid/squidCA.pem
always_direct allow all
sslproxy_cert_error allow all
sslproxy_flags DONT_VERIFY_PEER
#http_access deny !Safe_ports
#http_access deny CONNECT !SSL_ports
#http_access allow localhost manager
#http_access deny manager
#http_access allow localhost
#http_access allow local
#http_access deny all
#http_port 192.168.20.1:3128 intercept
#https_port 192.168.20.1:3129 intercept ssl-bump cert=/etc/squid/squidCA.pem
#sslcrtd_program /usr/lib/squid/ssl_crtd -s /var/lib/ssl_db -M 4MB
#coredump_dir /var/spool/squid
#refresh_pattern ^ftp: 1440 20% 10080
#refresh_pattern ^gopher: 1440 0% 1440
#refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
#refresh_pattern (Release|Packages(.gz)*)$ 0 20% 2880
#refresh_pattern . 0 20% 4320Answer the question
In order to leave comments, you need to log in
For a normal squid, it is enough to block the exit bypassing the proxy.
Squid without bumping is practically useless now - everything is on https. Without bumping, the site is captured from CONNECT, which may not be where the user went.
I already gave an example:
a user creates a site with a dull production name metricheskiy-krepeg.ru (or something else, but such that it matches the theme of production and makes admins feel discouraged :) ). And internally makes a page with transitions to VKontakte, love.mail.ru and tightwetholes.com :)
Question: what will the admin see in the proxy log
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question