Answer the question
In order to leave comments, you need to log in
Squid https filtering without certificate spoofing. How to solve the problem with ssl3?
OS: Debian 8.2 jessie
squid: 3.5.8 - with ssl support
openssl: 1.0.1k
Squid built as follows:
apt-get install git fakeroot build-essential devscripts
apt-cache policy squid3
apt-get build-dep squid3
apt-get build-dep libecap2
apt-get install libssl-dev libgnutls28-dev
vim /etc/apt/sources.list
# deb-src http://ftp.de.debian.org/debian/ testing main contrib non-free
apt-get update
apt-get source squid3/testing
apt-get source libecap3/testing
cd libecap-1.0.1/
dpkg-buildpackage -us -uc -nc -d
apt-get purge libecap2
dpkg -i libecap3_1.0.1-2_i386.deb
dpkg -i libecap3-dev_1.0.1-2_i386.deb
links squid-cache.org
cd squid3-3.5.7/
uupdate -v 3.5.8 ../squid-3.5.8.tar.gz
cd ../squid3-3.5.8/
vim debian/rules
# --enable-ssl
# --enable-ssl-crtd
# --with-openssl
dpkg-buildpackage -us -uc -nc
apt-get install squid-langpack
dpkg -i squid-common_3.5.8-1_all.deb
dpkg -i squid_3.5.8-1_i386.deb
dpkg -i squid3_3.5.8-1_all.deb
dpkg -i squidclient_3.5.8-1_i386.debiptables -F
iptables -P INPUT ACCEPT
iptables -P OUTPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -A FORWARD -i eth0 -o eth1 -j ACCEPT
iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT
iptables -t nat -A PREROUTING -i eth1 -p tcp --dport 80 -j REDIRECT --to-port 3128
iptables -t nat -A PREROUTING -i eth1 -p tcp --dport 443 -j REDIRECT --to-port 3129acl localnet src 192.168.15.0/24
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow localhost manager
http_access deny manager
http_port 192.168.15.237:3128 transparent
acl blacklist url_regex -i "/etc/squid/blacklist"
http_access deny blacklist localnet
http_access allow localnet
https_port 192.168.15.237:3129 intercept ssl-bump connection-auth=off options=ALL cert=/etc/squid/squidCA.pem
always_direct allow all
sslproxy_cert_error allow all
sslproxy_flags DONT_VERIFY_PEER
ssl_bump peek all
acl blocked ssl::server_name .vk.com .google.ru .google.com
ssl_bump terminate blocked
ssl_bump splice all
coredump_dir /var/spool/squid
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern .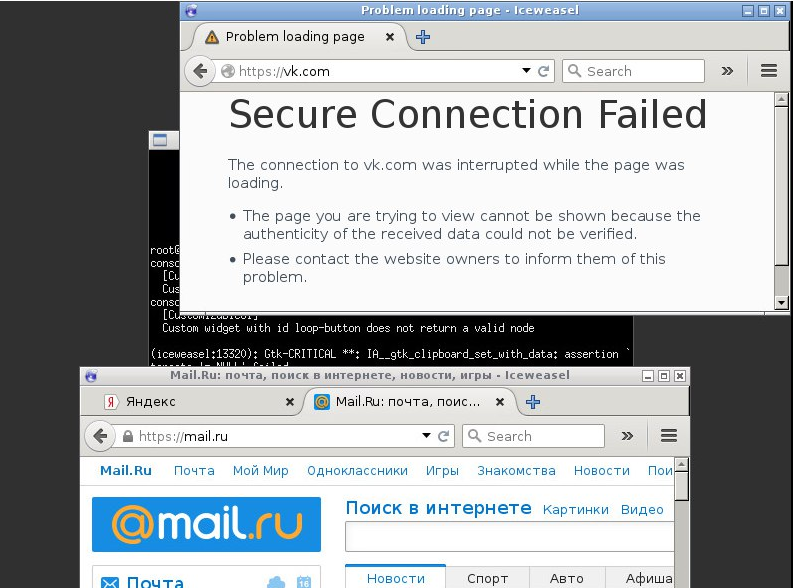
curl --sslv3 https://ya.ru, the curl client hangs and squid throws an error. [email protected]:~# tail -f /var/log/squid/cache.log
2015/09/19 10:02:08 kid1| HTCP Disabled.
2015/09/19 10:02:08 kid1| Pinger socket opened on FD 16
2015/09/19 10:02:08 kid1| Squid plugin modules loaded: 0
2015/09/19 10:02:08 kid1| Adaptation support is off.
2015/09/19 10:02:08 kid1| Accepting NAT intercepted HTTP Socket connections at local=192.168.15.237:3128 remote=[::] FD 13 flags=41
2015/09/19 10:02:08 kid1| Accepting NAT intercepted SSL bumped HTTPS Socket connections at local=192.168.15.237:3129 remote=[::] FD 14 flags=41
2015/09/19 10:02:08| pinger: Initialising ICMP pinger ...
2015/09/19 10:02:08| pinger: ICMP socket opened.
2015/09/19 10:02:08| pinger: ICMPv6 socket opened
2015/09/19 10:02:09 kid1| storeLateRelease: released 0 objects
2015/09/19 10:02:27 kid1| Error negotiating SSL on FD 15: error:14077102:SSL routines:SSL23_GET_SERVER_HELLO:unsupported protocol (1/-1/0)acl localnet src 192.168.15.0/24
acl trustedman src 192.168.15.1
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow localhost manager
http_access deny manager
http_port 192.168.15.237:3128 transparent
acl blacklist url_regex -i "/etc/squid/blacklist"
http_access deny blacklist localnet
http_access allow localnet
https_port 192.168.15.237:3129 intercept ssl-bump options=ALL:NO_SSLv3:NO_SSLv2 connection-auth=off cert=/etc/squid/squidCA.pem
always_direct allow all
sslproxy_cert_error allow all
sslproxy_flags DONT_VERIFY_PEER
acl blocked ssl::server_name .vk.com .google.ru .google.com
acl step1 at_step SslBump1
ssl_bump peek step1
ssl_bump terminate blocked !trustedman
ssl_bump splice all
sslcrtd_program /usr/lib/squid/ssl_crtd -s /var/lib/ssl_db -M 4MB
coredump_dir /var/spool/squid
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320Answer the question
In order to leave comments, you need to log in
I installed Squid on a separate server with Arch x64, everything works perfectly with this config, nothing crashes and no errors appear. As far as I understand, the problem is in the specific patches that are applied in Debian Squid, but there are none on Arch, Squid is more "vanilla" there . I think the topic can be closed
perhaps the problem is due to an attempt to use transparent proxying without prescribing a proxy in the browser
for SSL it doesn't work
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question