Answer the question
In order to leave comments, you need to log in
Pygost, parsing a public key from a certificate. Wrong key?
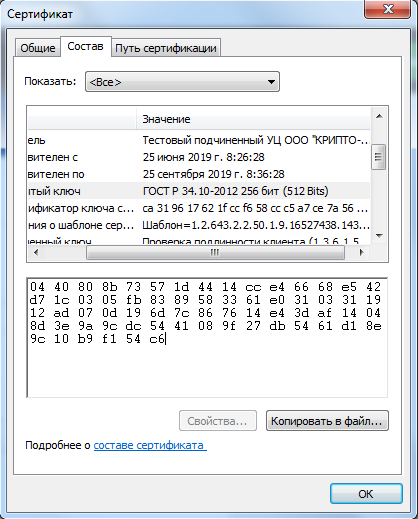 I can parse the certificate and extract the public key from there. But attempts to verify the signature made by this certificate give a negative result - the values do not match. I believe this may be due to:
I can parse the certificate and extract the public key from there. But attempts to verify the signature made by this certificate give a negative result - the values do not match. I believe this may be due to:
b'\x80\x8b\x73...'(excluding bytes 04 40 )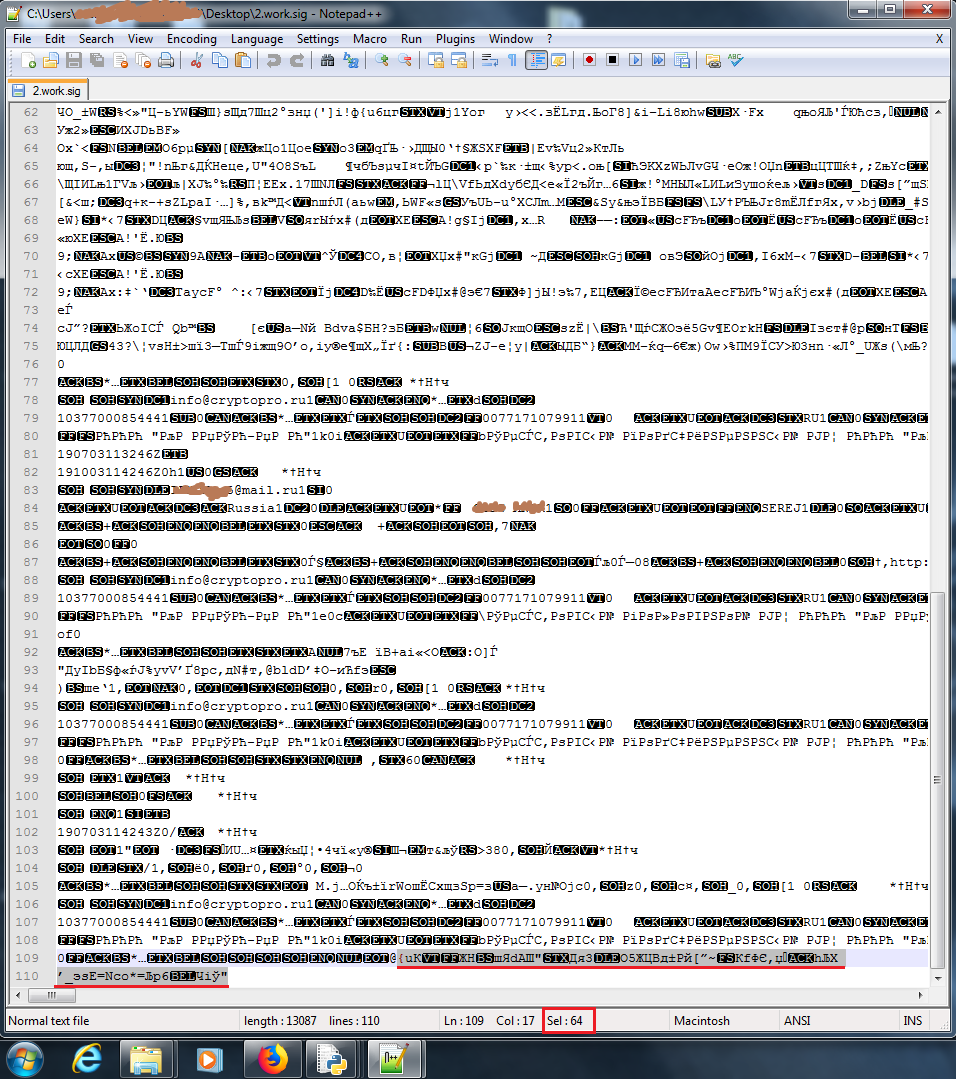
Answer the question
In order to leave comments, you need to log in
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question