Answer the question
In order to leave comments, you need to log in
Polkit policy domain groups?
Hello, can anyone come across, or tell me,
I’m doing a config for polkit (the meaning is that password requests are not displayed for AD users in RDP sessions)
[Do anything you want]
Identity=unix-group:admin
Action=*
ResultActive=yesAnswer the question
In order to leave comments, you need to log in
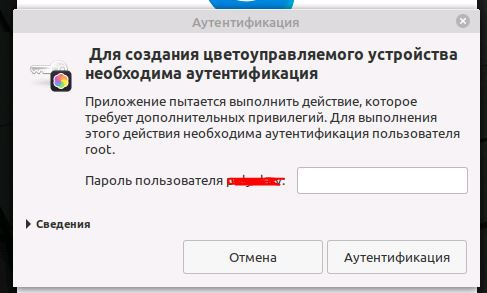
It depends on what action the password request provokes : you
can look in the "details" in the request window, then it will come in handy
. /localauthority/xx-xxxx we create .pkla files, we take the name itself from the "information".
Specifically, in my case, it turned out to remove the root password requests for network manipulation (enable/disable PPTP) as follows: I added the following content to the
/etc/polkit-1/localauthority/10-vendor.d/org.freedesktop.NetworkManager.pkla file
:
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question