Answer the question
In order to leave comments, you need to log in
Mikrotik router and 3 networks. Maybe?
The organization has 3 networks:
1. Provider network 5.44.12.0/24 (conditionally)
2. Enterprise main network 10.10.1.0/16
3. Camera network 10.10.5.0/24.
It is necessary to make it so that networks 2 and 3 saw each other (routed) and both had access to network 1 (Internet provider).
Do I understand correctly that for this I need a router with 3 ports and nothing else? If you purchase a MIKROTIK RB3011UIAS-RM router, can you set up such a scheme there?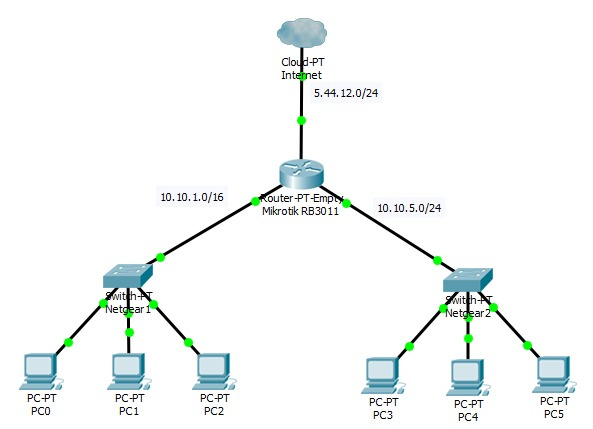
Answer the question
In order to leave comments, you need to log in
you can separate two networks into separate VLANs, connect them with a switch, create a trunk port with access to 2 vlans, connect it to one Mikrotik port (if it supports tagging, of course), create two virtual interfaces under the corresponding vlans, and route. In this way, in principle, you can not only connect 2 networks.
Do I understand correctly that for this I need a router with 3 ports and nothing else? If you purchase a MIKROTIK RB3011UIAS-RM router, can you set up such a scheme there?
It is possible to do. The easiest way:
eth1 - Internet
eth2 - locale 1 (dhcp - pool1)
eth3 - locale 2 (dhcp - pool1)
by default, locale1 and locale2 are freely routable, and go to each other and to the Internet. Next, you configure the firewall, how and what should go. Let's say from LAN 1 to LAN 2 certain ports are allowed.
By default, all networks are routed to MikroTik, connection routes appear.
Your networks 10.10.1.0/16 and 10.10.5.0/24 intersect. More precisely, the second is part of the first. This is fraught with ....
You can get by with one port on Mikrotik towards the local network. In this case, two subnets will hang on the interface, and all devices in the local network will not be isolated at the L2 level (all will be in the same Ethernet segment). But it's not pretty (fu-fu-fu).
It is better, of course, to install managed switches, divide the segments into different VLANs, make a DMZ (if necessary), configure Loopback detection, DHCP spoofing, security policies, QOS policies, etc., etc.
I am crazy about advice, although maybe 2 years ago it was relevant ... but now everything is done in one of the following ways (in fact, there are a lot of nuances here): the
bridge should not be between 2 and 3
solutions:
1. Mikrotik should be a gateway and distribute DHCP to both networks with the add default forwarding checkbox enabled.
2. Mikrotik is a gateway, all devices are static and you manually prescribe a route for all 3 networks, but in this case there are 3 of them (1 external network, 2 LANs with 16 masks, 3 LANs with 24 masks).
Vlan is not needed if there are 2 physically different switches (and in terms of money it will be much cheaper to be honest). If you still want 1 switch, then you need an l2 switch, then everything is driven through Vlan, only you will need 2 ports, although you can have 3, if you configure l2 correctly, there will be no loop, and the throughput will grow, but as for me it is unnecessary game if you have ports for example 1gb / s, and for example there are less than 30 cameras and they are all 4k in h264 + / h265 + with continuous recording. But if there are a lot of cameras and they are shitty, I would divide the cameras into groups of 4/8pcs per vlan and naturally there would be more networks in this situation (for example, I have 300+ of these networks and each is routed according to its own rule).
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question