Answer the question
In order to leave comments, you need to log in
Is there a DDoS or has my server been hacked?
Some time ago I bought a server from EOMY for training / tests, etc. Today I’m trying to log in via SSH, but I couldn’t because the server was turned off, when I entered the PU by the server ( http://billing.it7.net) I found this error: 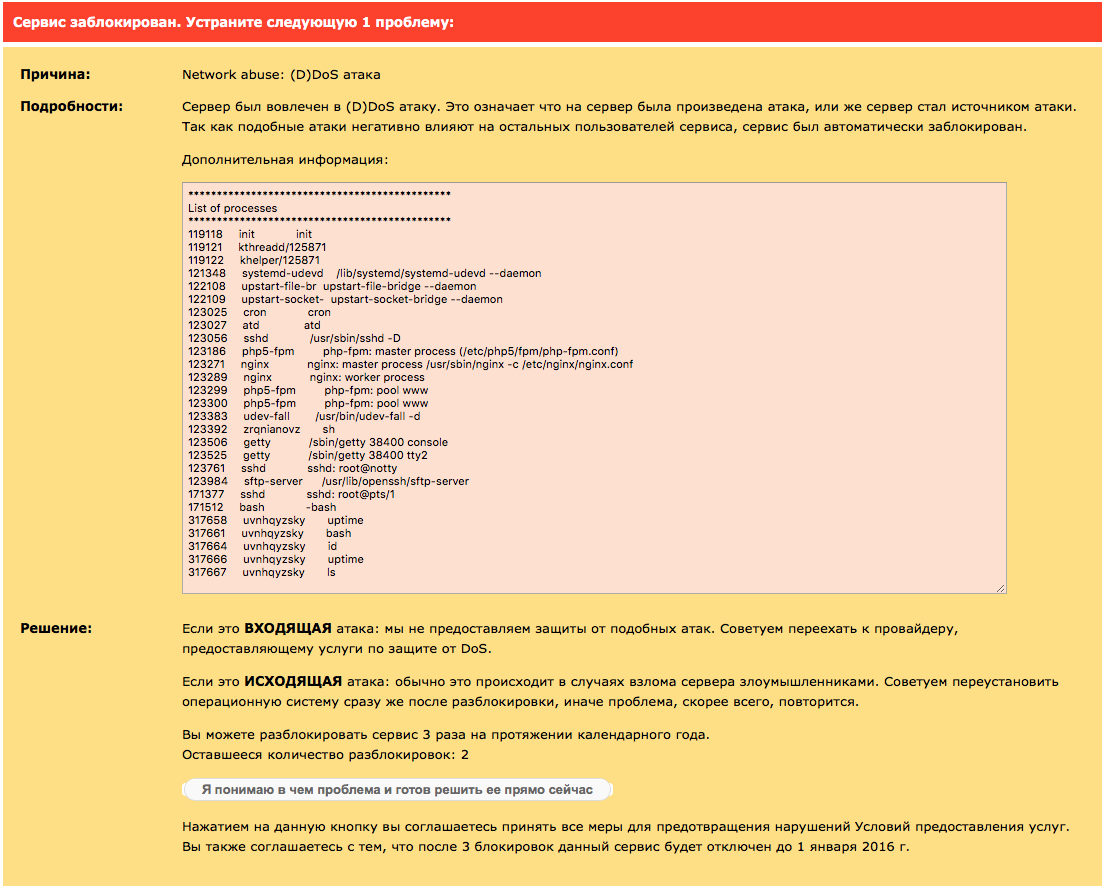
I decided to copy all the files from the server, reinstall the system and configure at least some then DDoS protection. I turned on the server, changed the password, but before I had time to copy all the information, the server "fell down" again.
While I was on the server, I decided to look into the nginx logs, I saw a huge number of requests to non-existent pages.
I don’t understand what could be the matter, is it my DDoS server or me? And what's the point of DDoSing a site that has absolutely nothing on it?
UPD: I add logs, those that are located below the process sheet.
***************************************************
First 260 lines from conntrack table (truncated)
********************************************* *
ipv4 2 tcp 6 109 SYN_SENT src=MY_IP dst=115.231.231.131 sport=54383 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=54383=0 secmark=0 use=2
cipv4 2 tcp 6 109 SYN_SENT src=MY_IP dst=115.231.231.131 sport=58341 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=58341 mark=0 secmark=0 use=2
ipv4 2 tcp 6_SENT src =MY_IP dst=115.231.231.131 sport=53381 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=53381 mark=0 secmark=0 use=2
ipv4 2 tcp 6 110 SYN_SENT src=MY_IP dst=115.231.231.131 sport=33379 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=33379=0 secmark= mark0 use=2
tcpv4 6 109 SYN_SENT src=MY_IP dst=115.231.231.131 sport=30695 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=30695 mark=0 secmark=0 use=2
ipv4 rc 2 tcp 6 109 SYN_SENT MY_IP dst=115.231.231.131 sport=46317 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=46317 mark=0 secmark=0 use=2
ipv4 2 tcp 6 110 SYN_SENT src=11MY_IP dst=1 .231.131 sport=16250 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=16250 mark=0 secmark=0 use=2
ipv4 2 tcp 6 109 SYN_SENT src=MY_IP dst=115.231.231.131 sport=36300 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=36300=0 secmark= mark0 use=2
tcpv4 6 109 SYN_SENT src=MY_IP dst=115.231.231.131 sport=45592 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=45592 mark=0 secmark=0 use=2
ipv4 rc 2 tcp 6 109 sENT=SENT MY_IP dst=115.231.231.131 sport=23728 dport=80 [UNREPLIED] src=115.231.231.131 dst=MY_IP sport=80 dport=23728 mark=0 secmark=0 use=2
Answer the question
In order to leave comments, you need to log in
Most likely, they picked up the password from ssh and are now using the server as a host for the attack. What's the point of ddosing the training server? Change passwords and set up iptables
Hacking on the face, most likely picked up the password from SSH, which is apparently spinning on the standard port 22.
- Change the port;
- Set up authorization by key, disable the password altogether;
- For fidelity, you can do two-factor authorization;
- All unnecessary to close Iptables, as advised above.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question