Answer the question
In order to leave comments, you need to log in
Is the following implementation of AES 128 CTR encryption secure?
I implement AES 128 CTR encryption. Implemented, works, blocks match. But still there are some doubts about the reliability of my implementation, therefore, I ask knowledgeable people to help.
The original file is taken and the key is taken. The file is divided into blocks of 16 bytes ( 128 bits). The file is not always split entirely, so if the file length in bytes is not a multiple of 16 byte 0x01 is written to the end of the last block , and the remaining space in the block (if any) is filled with 0x00 bytes . If the length of the file in bytes is a multiple of 16 , then another block is created at the beginning of which is byte 0x01 , and all other bytes are 0x00. Further, all these blocks are encrypted using AES 128 CTR . CTR mode uses a counter for encryption, and without it the file cannot be decrypted. The counter, which occupies 16 bytes, is written immediately after the encrypted blocks, and the counter is not encrypted. Further, after the counter, a block with the KCV key is written (the first 6 bytes of the block are KCV , the remaining ten bytes are 0x00 ). KCV is also not encrypted.
In total, the encrypted file looks something like this. Can this scheme be considered secure, and if not, what can be done to ensure cryptographic security?
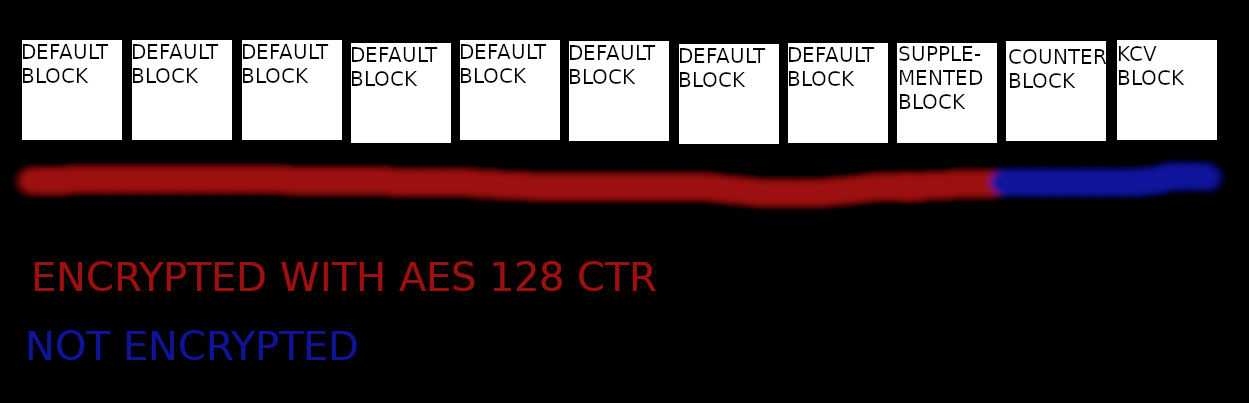
PS KCV I think according to the definition from Wikipedia. I take a block consisting exclusively of bytes 0x01 , encrypt it with a key, and take the first 6 bytes of the block as the KCV of the key. A similar operation is needed to check the correctness of the key during decryption.
Answer the question
In order to leave comments, you need to log in
The first answer that comes to my mind when I see a crypto bike is that it is dangerous and safe at the same time. It is dangerous because no one knows about it - which means that no one uses it and experts do not look for holes in it. Well, it's safe for the same reason.
At a minimum, the ability to check the correctness of the key during decryption should be optional - because this is a great help for brute force. If the user got confused when typing the password - SSZB.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question