Answer the question
In order to leave comments, you need to log in
How to set up Fail2ban on Mikrotik?
I'm trying to set up conditional fail2ban on Mikrotik CCR-1016, based on the official documentation
https://wiki.mikrotik.com/wiki/Bruteforce_login_pr... :
1) add chain=input protocol=tcp dst-port=22 connection-state=new action=add-src-to-address-list \
address-list=ssh_stage1 address-list-timeout=1m comment="" disabled=no
(помечаем любые попытки залогиниться в список ssh_stage1 на 1 минуту)2) add chain=input protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage1 \
action=add-src-to-address-list address-list=ssh_stage2 address-list-timeout=1m comment="" disabled=no
(вторую попытку подключения c ip заносим со списка ssh_stage1 в список ssh_stage2 также на 1 минуту)3) add chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage2 action=add-src-to-address-list address-list=ssh_stage3 \
address-list-timeout=1m comment="" disabled=no
(третью попытку подключения также заносим из ssh_stage2 в ssh_stage3 и также на 1 минуту)4) add chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage3 action=add-src-to-address-list address-list=ssh_blacklist \
address-list-timeout=10d comment="" disabled=no
(четвертая и последующие попытки должны отправляться в банлист на 10 дней)5) add chain=input protocol=tcp dst-port=22 src-address-list=ssh_blacklist action=drop \
comment="drop ssh brute forcers" disabled=no
(собственно, бан всех, кто в ssh_blacklist)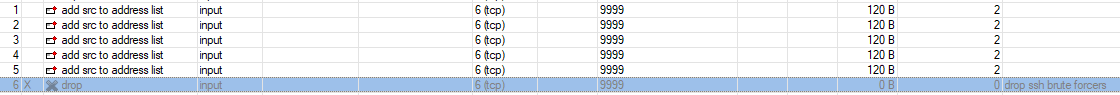
Answer the question
In order to leave comments, you need to log in
So, make another list. white list and just add to the rules, if src adress is not in the white list, then we follow the rules.
Either the first rule checks for SSH and white list, then jump to the rest of the rules
add action=add-src-to-address-list address-list=blocked_honeypot address-list-timeout=1w1s chain=input connection-state=new in-interface=ether1 protocol=tcp src-address-list=!admin src-port=3389,22,8291
add action=drop chain=input src-address-list=blocked_honeypotDidn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question