Answer the question
In order to leave comments, you need to log in
How to properly network in Proxmox using pfSense?
There is a dedicated Hetzner server with one network interface (for example 42.88.80.15 (GT 42.88.80.1)) and 3 additional IP addresses (for example 42.88.80.27, 42.88.80.30, 42.88.79.152 (GT 42.88.79.225)). The server has Proxmox installed with virtual machines and containers. Two web servers use IP 42.88.80.27, 42.88.80.30. 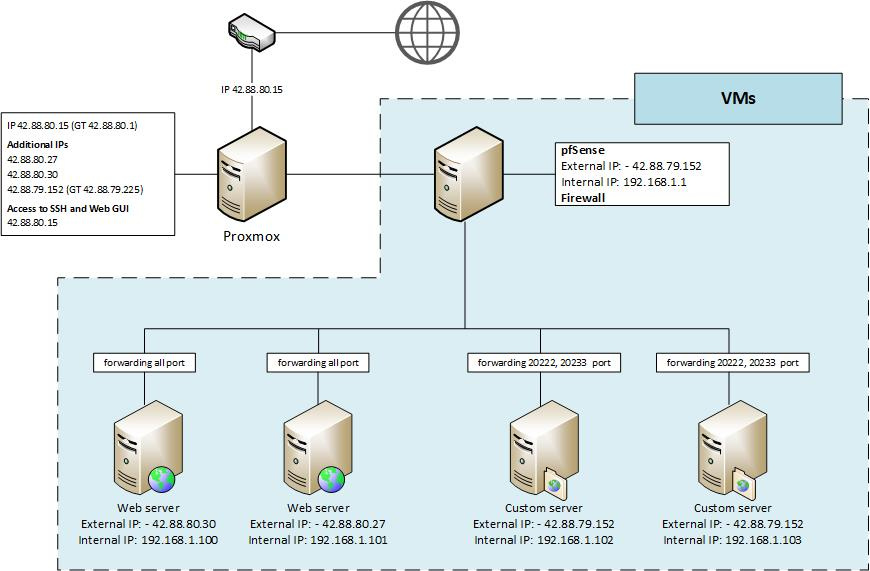
One virtual machine has pfSense (Virtual Machines) installed, which acts as a gateway. Through it passes traffic to other virtual machines. Two virtual machines (on a Linux Container) use dedicated IPs, the others use the IP address of the machine where pfSense is installed.
Now the Proxmox server is configured with:
Answer the question
In order to leave comments, you need to log in
This scheme works for me, but with MIkrotik.
I added 6 interfaces (according to the number of additional IPs) looking in vmbr0 (the external interface of the server is also included there. MAC and naturally taken from the Robot.
Next, I made a LAN interface looking in vmbr1 (where all virtual machines are connected) and cut vlan- s. Accordingly, in the network settings of KVM machines and LXC containers, I specify not only the vmbr1 interface, but also the required vlan.
Mikrotik is configured with Source policy routing, a rake - you need to explicitly specify gateway interfaces, because Hetzner most often additional IPs come from the same network and with one GW.
The question is not very clear, as the answer is given in the picture.
Just do it on her
There is some useful information here:
https://docs.netgate.com/pfsense/en/latest/virtual...
Because the hardware checksum offload is not yet disabled, accessing pfSense webGUI might be sluggish. This is NORMAL and is fixed in the following step.
To disable hardware checksum offload, navigate under System > Advanced and select Networking tab. Under Networking Interfaces section check the Disable hardware checksum offload and click save. Reboot will be required after this step.
It is possible that the checksum verification settings on ProxMox slow down network packets.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question