Answer the question
In order to leave comments, you need to log in
How to overcome untrusted SSL certificate (COMODO)?
The third day I dance with a tambourine. I am preparing a server for PCI DSS (payment card industry data security standard). All problems are eliminated, but there is one that can not be overcome. To check the server, a scanner is used ( https://www.hackerguardian.com/), which constantly gives one problem: SSL Certificate Cannot Be Trusted 443 / tcp / www
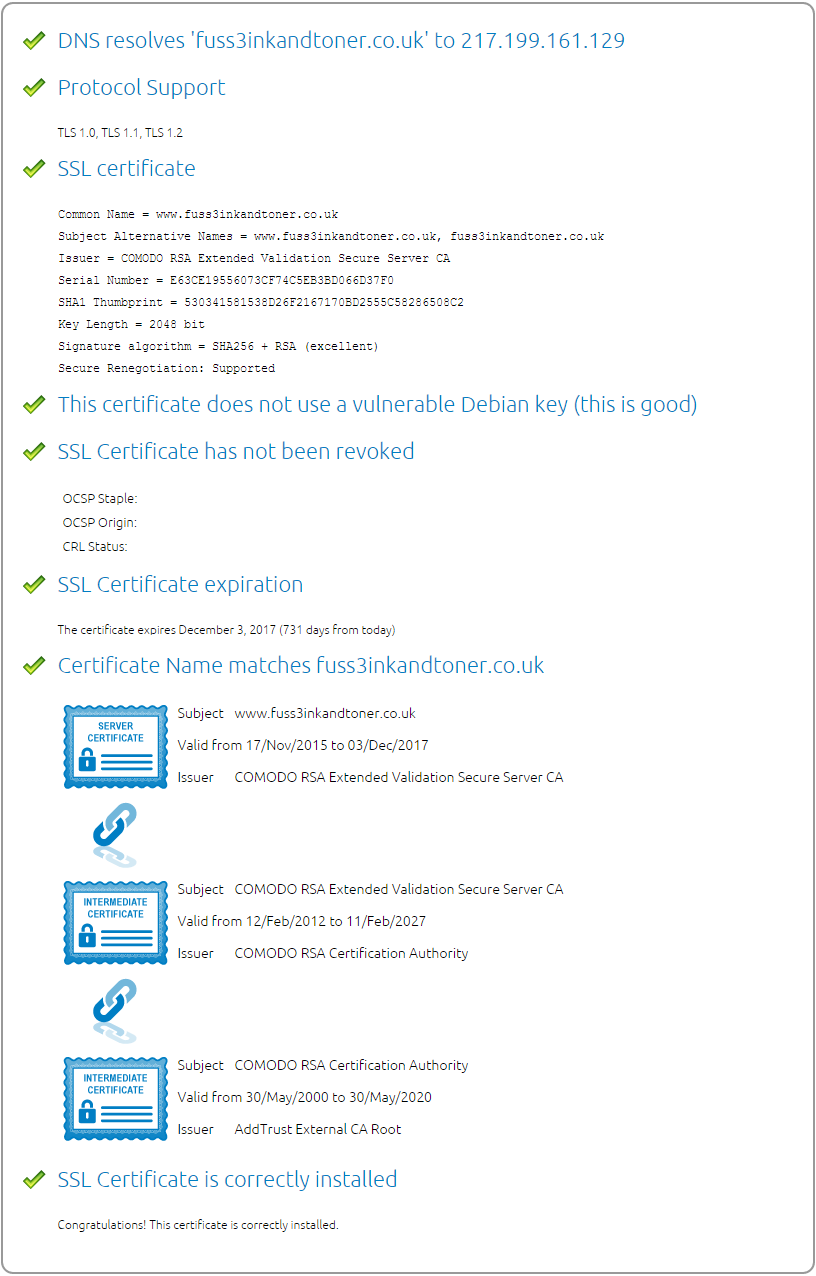
I removed all the certificates from the chain and left only one specially purchased for this server. It is signed by COMODO. They seem to be among the most reliable. Here is the certificate dump:
openssl x509 -in /usr/local/psa/var/certificates/cert-f1nb7M -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
e6:3c:e1:95:56:07:3c:f7:4c:5e:b3:bd:06:6d:37:f0
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO RSA Extended Validation Secure Server CA
Validity
Not Before: Nov 17 00:00:00 2015 GMT
Not After : Dec 3 23:59:59 2017 GMT
Subject: serialNumber=04045342/1.3.6.1.4.1.311.60.2.1.3=GB/businessCategory=Private Organization, C=GB/postalCode=BN27 2BY,
ST=East Sussex, L=Hailsham/street=Station Road/street=Unit 10 Swan Business Centre, O=Fuss 3 Solutions Ltd,
OU=COMODO EV SSL, CN=www.fuss3inkandtoner.co.uk
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
...................
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Authority Key Identifier:
keyid:39:DA:FF:CA:28:14:8A:A8:74:13:08:B9:E4:0E:A9:D2:FA:7E:9D:69
X509v3 Subject Key Identifier:
D1:C0:72:40:F1:A4:47:A6:FF:32:C4:56:6F:EF:F5:1E:40:6A:72:DC
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Certificate Policies:
Policy: 1.3.6.1.4.1.6449.1.2.1.5.1
CPS: https://secure.comodo.com/CPS
X509v3 CRL Distribution Points:
Full Name:
URI:http://crl.comodoca.com/COMODORSAExtendedValidationSecureServerCA.crl
Authority Information Access:
CA Issuers - URI:http://crt.comodoca.com/COMODORSAExtendedValidationSecureServerCA.crt
OCSP - URI:http://ocsp.comodoca.com
X509v3 Subject Alternative Name:
DNS:www.fuss3inkandtoner.co.uk, DNS:fuss3inkandtoner.co.uk
1.3.6.1.4.1.11129.2.4.2:
............
Signature Algorithm: sha256WithRSAEncryption
...............
Answer the question
In order to leave comments, you need to log in
In general, it turned out to be a bug of the COMODO https://www.hackerguardian.com/ scanner : it seems to be not normal that the COMODO scanner swears at the certificate from them as unreliable. Everything was solved by marking this problem as false positive, their admins checked and confirmed it. So the issue is closed.
There was a similar problem, but perhaps not from that opera.
All browsers perceived the certificate as fake, I checked it on the same site as you, but I mozilla says that the certificate should not be trusted, in the end it turned out that I put the intermediate certificate instead of the root one. When I started to understand, I looked at the site reg.ru in their help they write that we put an intermediate one, I looked at GlobalSign, there they write the root
one. I don’t know if this information will help you.
It is necessary to combine the entire certificate chain into one and already use it myself, I encountered the same, this method helped me
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question