Answer the question
In order to leave comments, you need to log in
How to make vlan networks isolated from each other with access to wan?
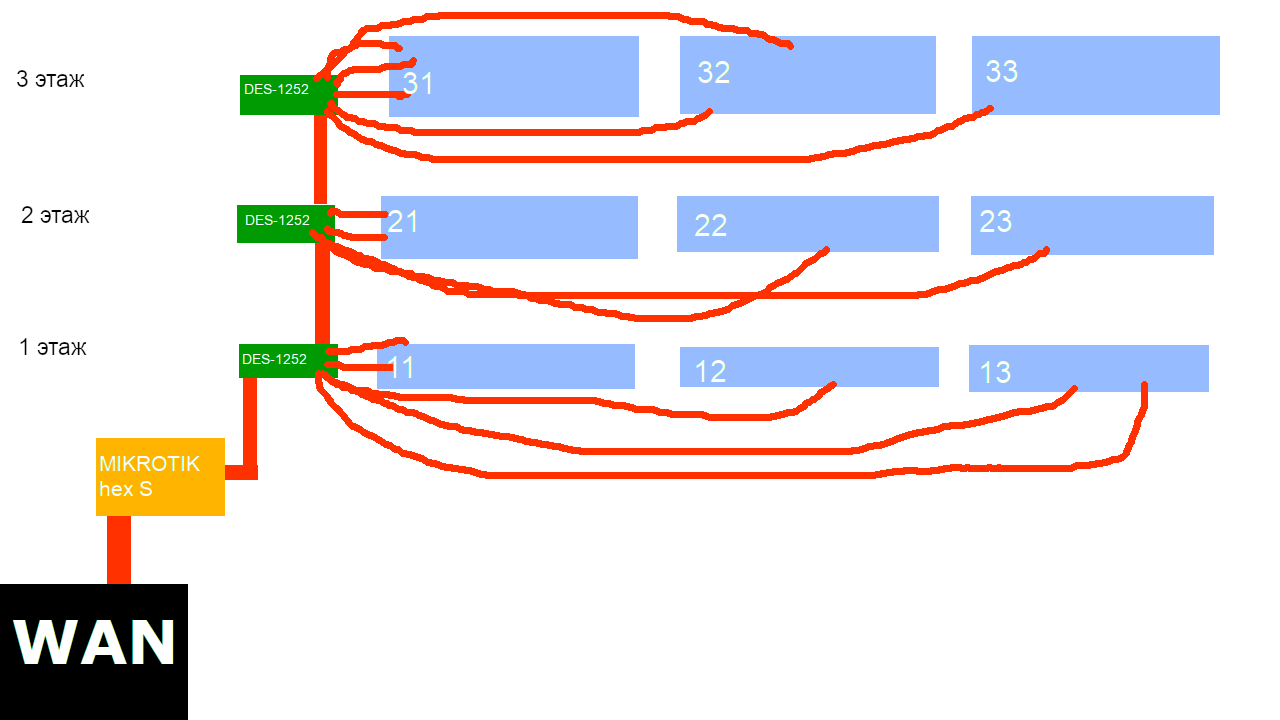
There is a network in the building with offices.
In this network, the main Mikrotik router (RouterOS level 4) and D-link DES-1252 switches.
This network is unmanaged, a pppoe server is set up on Mikrotik and offices to access the network, each computer in each office must connect via pppoe, Mikrotik does not issue an ip address and does not have a local ip address on the port, i.e. just at the L2 level it distributes the Internet via pppoe.
Each cabinet has from 1 to 4 Ethernet sockets, I want to make sure that some cabinets have their own subnet with access to the WAN and no access to other subnets. And other cabinets continued to use pppoe.
For example, room 21 subnet 10.0.21.0/24, room 32 subnet 10.0.32.0/24, room 33 no subnet pppoe only. As I understand it, VLAN allows you to do this. Now on switches everywhere by default VLAN1, in which all ports are untagged.
And in total, each port has three modes: tagged, untagged, not member.
I created vlan2 and added three untagged ports there (and made them not member in vlan1), as a result, hosts on these ports had their own l2 network.
But here's how to make this network see Mikrotik, but at the same time not see hosts from other vlans, and Mikrotik was a router (NAT), dhcp server and gateway to the Internet for this one. It may also sometimes be necessary to allow L3 traffic between several cabinets of your choice, it would be convenient to do this using Mikrotik's firewall permission rules.
How to implement it correctly?
Answer the question
In order to leave comments, you need to log in
There is a video on YouTube that describes a scheme similar to yours (router on a stick) https://www.youtube.com/watch?v=peJc8pM7duY only there pfsense acts as a router or network core. There is a book on setting up vlans in various configurations:

Here, about pppoe, just your topic in conjunction with pfsense is what you need.
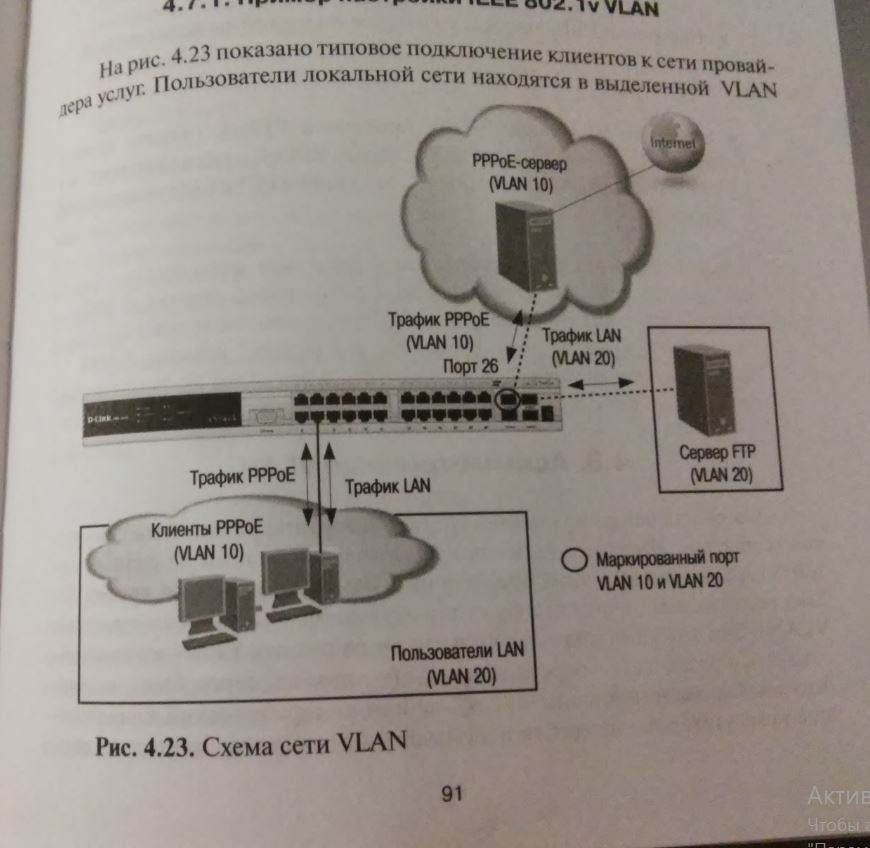
and continuation:

and asymmetric vlans for "But here's how to make this network see Mikrotik, but at the same time not see hosts from other vlans."
Simplified, you can consider vlan as separate cable networks with their own switches.
The terms for different switches may differ, so I’ll try to generalize:
the ports to which the end hosts are connected will be members of some specific vlan, and the ports of the mikrotik switch will include all vlan
will remain on mikrotik on the ports to the switches, register these vlans and configure the right rules for them
As long as Mikrotik will only allow or not computers in the internet - everything will be fine. But as soon as you want to drive something between computers from different vlans, Mikrotik will have to do routing, and then the bolivar will begin to choke ....
There is a solution - either a more powerful router, or an L2 + / L3 switch - that one can route packets at a switching speed (although there is less flexibility in terms of routing, but at least everyone usually knows how to acl)
So that the networks are not seen - ip> routes, there seems to be a 3rd tab. Write down from which subnet, to which - and put unrechabl
My option:
Create VLANs on Mikrotik with normal routing through nat, not pppoe. throw dhcp into each vlan.
Forward everything to dlinks and either manually register on the ports, or (ideally) if there are a lot of cabinets / users, then raise the radius and let the 802.1x switches scatter everyone themselves. In principle, you can also script the generation of networks on mikrotik.
Similar schemes are sometimes used by small providers.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question