Answer the question
In order to leave comments, you need to log in
How to install Let's Encrypt correctly if Nginx is a balancer and the site itself is on IIS?
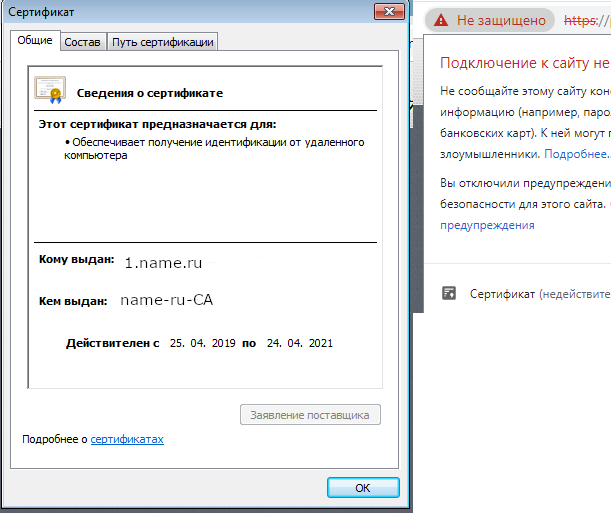
I've been googling for 4 days looking for information on getting a Let's Encrypt certificate. To receive a certificate, the site must be accessible from the outside.
I have this: a site on IIS under Windows Server 2008, available for the internal network, a balancer on Nginx under Ubuntu 12.04 (don't beat what you got, you got it), there are a lot of configs for different subdomains in /etc/nginx/conf.d like 1.name.ru, for one of these resources I need to configure https.
server {
server {
listen 80;
server_name 1.name.ru;
proxy_set_header Host 1.name.ru;
location / {
rewrite ^(.*)$ https://1.name.ru$1 permanent;
}
}
server {
listen 443 ssl;
server_name 1.name.ru;
ssl_certificate /etc/nginx/ssl/mycert.pem;
ssl_certificate_key /etc/nginx/ssl/mycert.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
set $srv_addr "https://xx.xxx.xxx.xx";
#charset koi8-r;
access_log /var/log/nginx/passport.access.log main;
proxy_set_header "Host" $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_connect_timeout 75s;
proxy_read_timeout 40m;
proxy_send_timeout 40m;
#types_hash_max_size 2048;
#client_header_buffer_size 16k;
#large_client_header_buffers 16 16k;
#request_pool_size 512k;
#client_body_buffer_size 5M;
#client_body_temp_path /tmp/nginx/client_temp 1 2;
client_max_body_size 50M;
#proxy_buffer_size 32k;
#proxy_buffers 16 64k;
#proxy_busy_buffers_size 128k;
#proxy_temp_file_write_size 128k;
# proxy_intercept_errors on;
location / {
proxy_pass $srv_addr;
proxy_no_cache 1;
proxy_cache_bypass 1;
#proxy_pass_header Set-Cookie;
#proxy_pass_header Host;
proxy_set_header "Host" $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_temp_path /var/nginx/proxy_temp;
client_body_temp_path /var/nginx/client_body_temp;
}
location ~* \.(js|css)$ {
proxy_pass $srv_addr;
proxy_no_cache 1;
proxy_cache_bypass 1;
#proxy_pass_header Set-Cookie;
#proxy_pass_header Host;
proxy_set_header "Host" $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_temp_path /var/nginx/proxy_temp;
client_body_temp_path /var/nginx/client_body_temp;
expires -1;
proxy_cache_valid 0;
proxy_ignore_headers X-Accel-Expires Expires Cache-Control;
}
}
wget https://dl.eff.org/certbot-auto
sudo mv certbot-auto /usr/local/bin/certbot-auto
sudo chown root /usr/local/bin/certbot-auto
sudo chmod 0755 /usr/local/bin/certbot-autoAnswer the question
In order to leave comments, you need to log in
Just add
location ^~ /.well-known/acme-challenge/ {
root /var/www/_letsencrypt;
}Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question