Answer the question
In order to leave comments, you need to log in
How to get external address for Mikrotik using remote pfSense on VPS?
Hello.
Advise, please, where to dig and what kind of infrastructure to pile up here in order to solve the problem.
My networking knowledge is poor. Especially in the place where routing and VPN without creating interfaces.
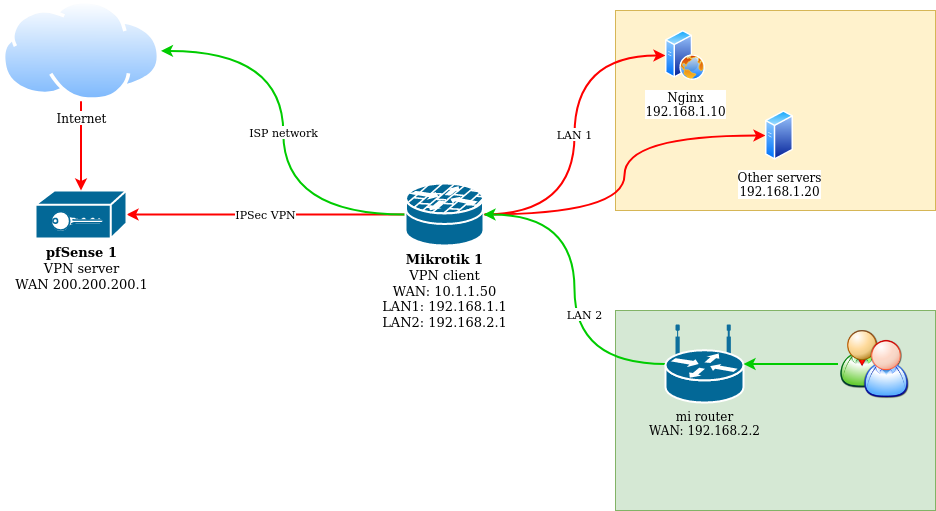
Given
1. Home Internet with gray IP (Mikrotik 1)
2. Virtual router in the cloud with one interface and white IP (pfSense 1)
3. Services in the internal network that need access from outside
4. Home Internet users.
I would like
1. Roughly speaking - connect from the outside to internal services, by forwarding ports to them.
For example, when connecting to http://200.200.200.1:80, get to 192.168.1.10:80 (see diagram).
2. Users continue to go to the Internet through the provider's network, and not through the VPN.
3. Users (LAN1) can access the service network (LAN2) using certain addresses and ports allowed on the Mikrotik firewall.
4. Mikrotik supports IPSec hardware encoding. I would like to use this functionality.
Questions
1. Is the task and scheme described in general clear?
2. How does an IPSec tunnel work? Mikrotik will have an additional address? On what interface? How in general will port forwarding be implemented on Mikrotik in this scheme?
3. What else did I not consider?
Answer the question
In order to leave comments, you need to log in
If I understand the task correctly (in my example):
1. An external VPN server is created with ip 123.123.123.123
2. An IPSec / IKE2 tunnel is raised on Mikrotik to the VPN server, and if there is no task to direct traffic that goes outside from the internal Mikrotik users in VPN, then in 'IP-> Mangle' we do not prescribe anything.
3. On Mikrotik, in 'IP->NAT', ALL traffic is forwarded (you can specify a specific port instead of all traffic, if there are several identical servers, or you need to specify access from the outside to a specific address within the Mikotik network) to some internal resource, for example Samba server 192.168.1.20: settings, chain - 'dst-nat', ipsec policy - 'IPsec', 'action - 'dst-nat', To adresses - '192.168.1.20'. Basically everything
4. On the VPN server, we give the command to
sudo ipsec leases
look at the Mikrotik address inside the VPN network, let's say it is 10.100.0.13
5. On any remote machine connected to the server's VPN network 123.123.123.123, open the network environment, enter smb://10.100.0.13 (for Windows 'smb:' is not necessary), we see the shared folders of the Samba server. If you chose port forwarding routing, then for example smb://10.100.0.13:12001 -> 192.168.1.20, smb://10.100.0.13:12002 -> 192.168.1.21, smb://10.100.0.13:12003 - > 192.168.1.22 and so on.
Task 3 is not directly related to VPN, this is how you set up routing inside Mikrotik
Make a vpn server on pfsense.
Connect from Mikrotik to pfsense Next,
do port forwarding with pfsense>> Mikrotik's IP in your vpn
Next, if you need to forward the port from Mikrotik to the local server
You will also need to allow routing and this traffic in the firewall. Pfsense and Mikrotik
And I put CHR (Mikrotik on a virtual machine) on vps for 44 r per month)))
It seems that a simple article did not check https://habr.com/en/post/352576/
I did this https://habr.com /en/sandbox/115104/ (this is wrong /ip routeR ) you can here https://wiki.iphoster.net/wiki/%D0%9A%D0%B0%D0%BA_...
Raised a VPN server on it, I connected Mikrotik from home to him.
I set up the visibility of two networks via VPN (an article on the Internet connecting two offices via Mikrotik, something like this, routing is prescribed there) + masquerades for ppp connections (our VPN).
And I forwarded the port in the cloud microte to my NAS. Now I go to him even from the phone.
Well, or buy a white IP costs 100-150 rubles, even from a mobile operator.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question