Answer the question
In order to leave comments, you need to log in
How to forward VPN clients to the local network?
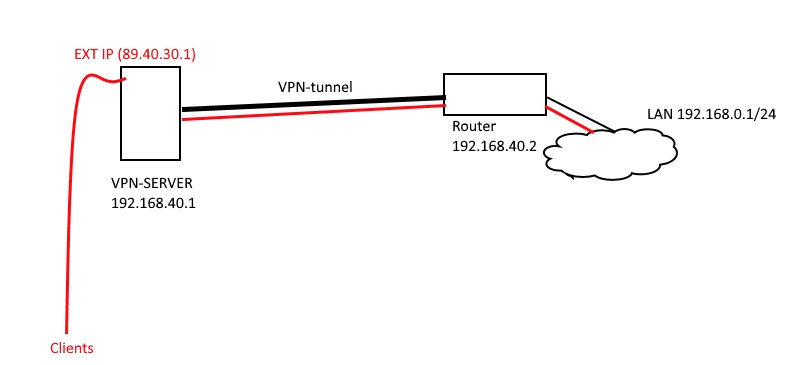
Good day. Such a problem - you need to organize a vpn channel between a remote server (CentOS) and the office. That is, the client must enter the external IP of the server and get into the internal office network via vpn.
The tunnel is up via PPTP, everything is fine, the router (Mikrotik) and the vpn server see each other. Nat rules have been added to iptables.
However, nothing is visible further than Mikrotik (although Mikrotik itself sees the LAN). Mikrotik creates the dynamic route to the vpn server itself, and sees it.
iptables config:
*nat
:PREROUTING ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A POSTROUTING -o eth0 -j MASQUERADE
-I PREROUTING -i eth0 -p tcp --dport 80 -j DNAT --to-destination 192.168.0.10
COMMIT
#
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -i eth0 -p tcp -m tcp --dport 1723 -j ACCEPT
-A INPUT -i eth0 -p gre -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A INPUT -p gre -j ACCEPT
-A INPUT -p tcp -m tcp --dport 1723 -j ACCEPT
-A FORWARD -i ppp+ -o eth0 -j ACCEPT
-A FORWARD -i eth0 -o ppp+ -j ACCEPT
-A FORWARD -i ppp+ -o ppp+ -j ACCEPT
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT192.168.0.1/24 via 192.168.40.2 dev ppp0Answer the question
In order to leave comments, you need to log in
IMHO, you need to register a route from 192.168.0.0/24 to 192.168.40.0/24 through 192.168.40.1 on microte.
most likely pings from 192.168.40.1 to 192.168.0.1 reach, but cannot return, do not know the route.
also check
192.168.0.1/24 via 192.168.40.2 dev ppp0
No, it didn’t work :(
Mikrotik sees the server, the server sees Mikrotik, but the server doesn’t see the LAN ...
Keywords "client-config-dir", "push", "route", "iroute".
The server needs to know which client is behind the 192.168.0.0/24 network.
For tun, it is done elementarily with the help of push routes to clients.
Since your connection is initiated only from the side of the client working through the VPN, it’s easier to raise another NAT on Mikrotik in the same way as a VPN server - this will allow you not to be driven with routing at intermediate points.
It will turn out like this - the VPN server NATs all packets from clients at 192.168.40.1, Mikrotik NATs 192.168.40.1 to its address 192.168.0.x
The second option is to raise the VPN server on Mikrotik. In general, you can do without a server.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question