Answer the question
In order to leave comments, you need to log in
How to distribute internet using netns and iptables?
The essence of the problem. There is a local network. There are several ip addresses from the provider. It is necessary that users of the local network behind nat be from different ip addresses, while all their traffic is processed by a network application, such as a redirector (not squid). Approximately according to the scheme below.
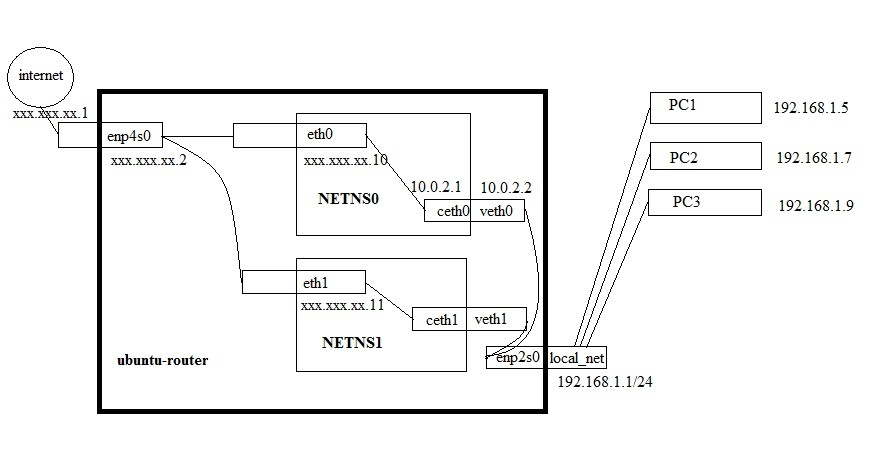
There is Internet which comes to the enp4s0 network device.
There is a local network that the enp2s0 network device looks into.
I create netns named netns0, it has 2 network devices inside:
1. eth0, which is a bridge to enp4s0 .
2. ceth0 that binds to veth0
Outside netns, there is an adapter called veth0 that binds to ceth0.
Through iptables, Internet distribution from enp4s0 to enp2s0 works without problems. But how to turn traffic from the enp2s0 local network to veth0, and redirect inside netns0 from the ceth0 interface to eth0 ?
List of commands used to create netns0 and configure interfaces,
ip netns add netns0
ip link add veth0 type veth peer name ceth0
ip link set ceth0 netns netns0
ip link set veth0 up
ip addr add 10.0.2.2/24 dev veth0
ip net exec netns0 ip link
ip net exec netns0 ip link set lo up
ip net exec netns0 ip link set ceth0 up
ip net exec netns0 ip addr add 10.0.2.1/24 dev ceth0
ip link add eth0 link enp4s0 type macvlan mode bridge
ip link
ip link set eth0 netns netns0
ip net exec netns0 ip link set eth0 up
ip net exec netns0 ip addr add xxx.xxx.xx.10/24 dev eth0
ip net exec netns0 ip addr sho dev eth0
ip net exec netns0 ip ra default via xxx.xxx.xx. 1 dev eth0
After that I try to distribute inside netns:
ip net exec netns0 sysctl net.ipv4.ip_forward=1
ip net exec netns0 iptables -A FORWARD -i eth0 -o ceth0 -m conntrack --ctstate NEW -j ACCEPT
ip net exec netns0 iptables -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
ip net exec netns0 iptables -A POSTROUTING -t nat -o eth0 -j MASQUERADE
And I try to wrap traffic from the local network to netns:
iptables -A FORWARD -i enp2s0 -o veth0 -m conntrack --ctstate NEW -j ACCEPT
iptables -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
iptables -A POSTROUTING -t nat -o veth0 -j MASQUERADE
But it fails. As I understand it, traffic to netns from the local network does not even try to run, although it works with the usual masquerade without netns. Ping from netns to the outside world goes fine, which means that the bridge between netns0 from eth0 to enp4s0 is working. But when trying to watch traffic inside netns, it is absolutely not there.
Answer the question
In order to leave comments, you need to log in
because you still need to configure traffic routing. ip rule and ip route are your friends in this matter
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question