Answer the question
In order to leave comments, you need to log in
Find cross-domain exchange scheme vulnerabilities?
We write a program for interaction between two domains. The essence of the problem: 2 domains, users from domain A go to the front in the domain under their accounts, the front under the technical account of domain B, sends a command to the back in domain B, which processes a very long task, after a while performs it and requests mail via LDAP user from domain A to send him the result of the execution to him by mail. Then sends the result to the user's mail. It is assumed that domain A (a domain with users) can be easily compromised, and why you need to contact an industrial domain from an untrusted domain, don't ask :) I'm
interested in what will happen if the fron is compromised and how to further develop attacks:
- requesting all data in a row from domain B;
- how to protect yourself from recipient mail spoofing (keep a separate database in domain B!?);
- what else could it be?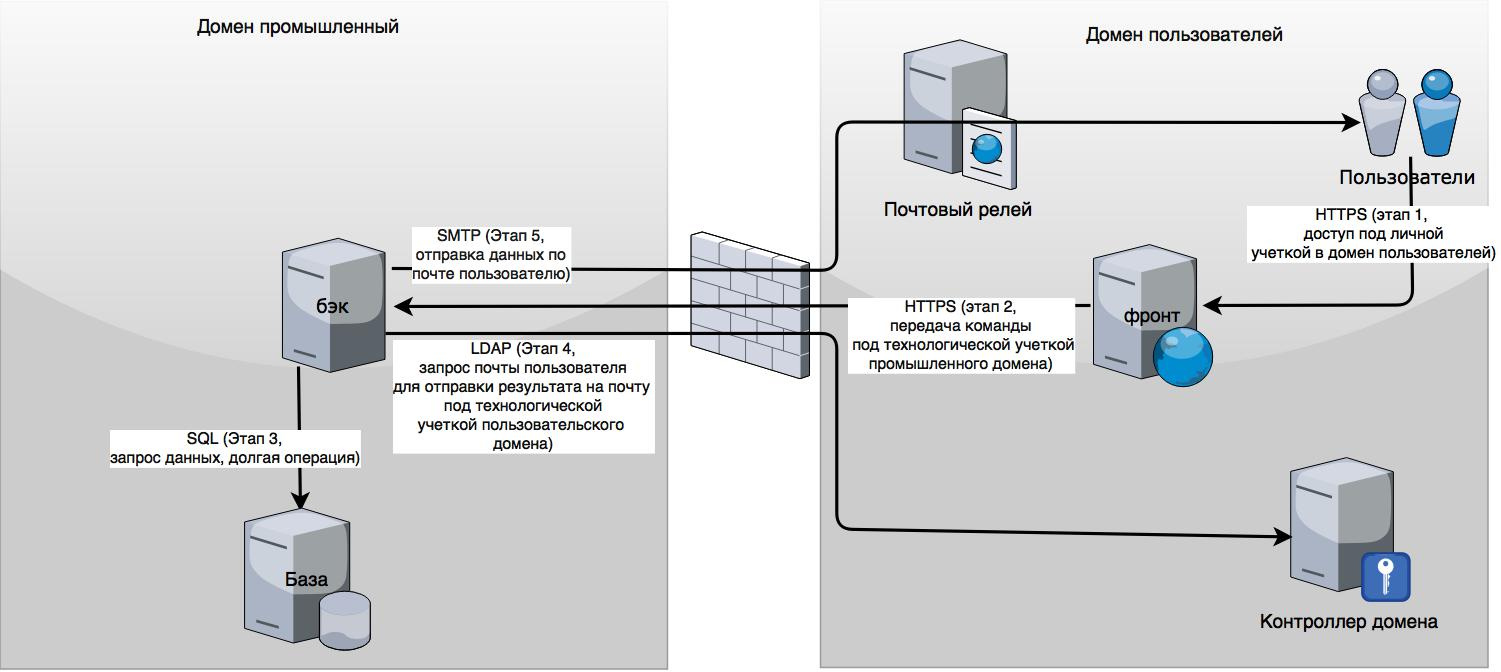
Answer the question
In order to leave comments, you need to log in
If you allow, I will discuss the example of web applications.
Server A is your client, B is your server.
Authentication and authorization is very similar to classic OAuth.
In case of hacking the client - disable the account on the server - 2 minutes.
Tasks must have an owner, in this case it is client A.
After disabling the account, the tasks are either destroyed or paused.
Mail must be sent by the client to the server at the time of task creation.
If the mail changes during the execution of the task, then A must change the task on the server B.
Your server B should not know anything about the clients at all. (In fact, there can be any number of)
The problems of requesting all the data in a row from the domain should be solved by a layer higher than the application. In an application, this is the authorization to access data.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question