Answer the question
In order to leave comments, you need to log in
Explain this site hacking scheme?
Greetings!
Yesterday I received a message from Yandex that one of my sites has been injected with malicious code, and of course, now the site is marked as dangerous in browsers.
The problem is that the site itself has not existed for several months - it was lying on a VPS from Digital Ocean, but due to the temporary irrelevance of the project, I completely deleted all droplets with projects from DO. That is, there was only a binding to the digital ocean DNS servers, registered in the domain registrar panel (2domains.ru).
When loading this seemingly non-existent site, this trash opens on my domain: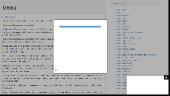
Moreover, it is clear that the page generated a large number of variations on the word "media" - this despite the fact that the word media is also present in the domain name itself. When the site is loaded, there is a subsequent redirect to the left resources with the order of prostitutes, etc....
Considering that I still had a binding to DNS DO on several abandoned domains, I immediately checked them too - as expected, the sites did not open , that is, with equal settings, this problem affected only one domain.
Naturally, I immediately changed all the DNS to the DNS of my registrar, but still I am very interested in how this hack happened, if it can be called a hack. Where did I overlook? Where was the weak link?
Answer the question
In order to leave comments, you need to log in
Well, someone put your domain on DO and uploaded it there. DNS is DO specified, so anyone could do it)
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question