Answer the question
In order to leave comments, you need to log in
CRS328/RouterOS + Cisco IP phone - how to start?
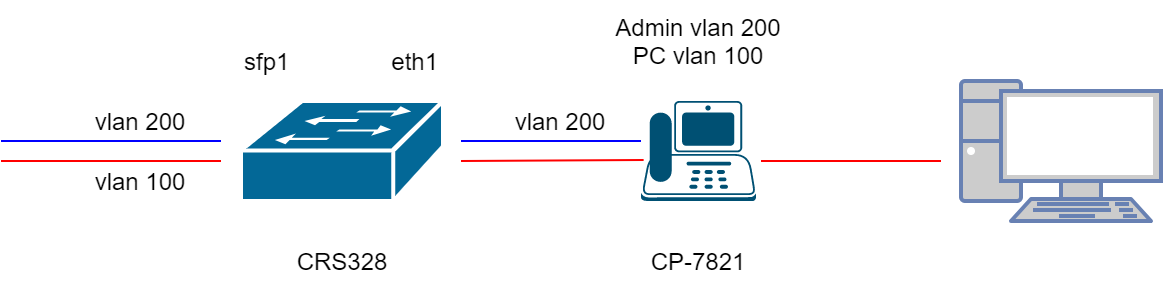
There is a CRS328 switch. On SFP1 it comes (simplifying) 2 vlan: 100 - for computers, 200 - for telephony. The CP-7821 phone is connected to the eth1 port, both vlans are served to it in Any mode with PVID 100. The phone is configured with Admin VLAN 200, PC VLAN 100. Everything is as in the illustration:
If the switch is in SwOS mode, the settings are as follows:
System tab: General section, Independent VLAN Lookup, IGMP Snooping checkboxes. Section DHCP & PPPoE Snooping, Trusted Ports - checkboxes for eth1 and sfp1
VLANs tab: start 2 vlan: 100 and 200. In these vlans, include the eth1 and sfp1 ports. Port Isolation and Learning are checked by default
VLAN tab: eth1 - VLAN Mode: enabled, VLAN Receive: any, Default Vlan ID: 100
sfp1 - VLAN Mode: enabled, VLAN Receive: only tagged, Default Vlan ID: 1
Everything is working. The phone registers, receives the TFTP configuration and network settings, calls, passes traffic to the computer (although it is not clear why register PC vlan if it should be untagged, but at least it works like that).
Reboot the switch in RouterOS
Config (minor omitted, L3 is nothing):
/interface bridge add add-dhcp-option82=yes dhcp-snooping=yes igmp-snooping=yes name=switch-bridge vlan-filtering=yes
/interface bridge port add bridge=switch-bridge frame-types=admit-only-vlan-tagged ingress-filtering=yes interface=sfp-sfpplus1 trusted=yes
/interface bridge port add bridge=switch-bridge interface=ether1 pvid=100 trusted=yes
/interface bridge vlan add bridge=switch-bridge tagged=sfp-sfpplus1 vlan-ids=100
/interface bridge vlan add bridge=switch-bridge tagged=sfp-sfpplus1,ether1 vlan-ids=200Answer the question
In order to leave comments, you need to log in
The solution turned out to be quite simple.
We add a rule to /interface ethernet switch rulewhich we set the desired vlan for traffic from the phone, and put things in order in other rules:
/interface bridge add add-dhcp-option82=yes dhcp-snooping=yes igmp-snooping=yes name=switch-bridge vlan-filtering=yes
/interface bridge port add bridge=switch-bridge frame-types=admit-only-vlan-tagged ingress-filtering=yes interface=sfp-sfpplus1 trusted=yes
/interface bridge port add bridge=switch-bridge interface=ether1 pvid=100
/interface bridge vlan add bridge=switch-bridge tagged=sfp-sfpplus1 untagged=ether1 vlan-ids=100
/interface bridge vlan add bridge=switch-bridge tagged=sfp-sfpplus1 untagged=ether1 vlan-ids=200
/interface ethernet switch rule add new-vlan-id=200 ports=ether1 src-mac-address=50:67:AE:00:00:00/FF:FF:FF:00:00:00 switch=switch1Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question