Answer the question
In order to leave comments, you need to log in
Cisco ACL parser, how to correctly?
Good afternoon! There is a problem in auditing large access lists from Cisco equipment. Here is an example (acl made up) :
object-group network AAAAAAAAAA
network-object 10.150.198.24 255.0.0.0
network-object 10.150.198.242 255.0.0.0
network-object 10.150.198.243 255.0.0.0
network-object 10.150.198.247 255.0.0.0
object-group network BBBBBBBBBBB
network-object 10.150.2.17 255.0.0.0
network-object 10.157.7.14 255.0.0.0
object-group service CCCCCCCCCCCCCC
service-object udp destination eq tftp
service-object udp destination eq sip
service-object udp destination eq 9999
service-object udp destination range 32768 61000
access-list OUTSIDE-IN extended permit udp object-group AAAAAAAAAAobject-group BBBBBBBBBBB range 8000 65535
access-list OUTSIDE-IN extended permit object-group BBBBBBBBBBB object-group AAAAAAAAAAobject-group CCCCCCCCCCCCCCparse = CiscoConfParse(args.file, syntax='ios', factory=True)
print(parse)
dict = {}
for net_obj in parse.find_parents_w_child('^object-group',''):
res = str(net_obj).split(' ')[2] # получаем название (id) объекта
dict[res] = []
print()
print()
print('!!!-----Найден объект: '+res+'--------------------')
print('Объект содержит следующие правила:')
for c_obj in parse.find_objects(res):
for ccobj in c_obj.children:
service_object = str(ccobj).split("'")[1]
service_object = service_object.replace('service-object','')
service_object = service_object.replace('network-object', '') #очищаем правило от лишних слов
print(service_object) #получаем чистую строку service object или network object
dict[res].append(service_object)
acl = []
for acl_obj in parse.find_objects(r'access-list'):
words = str(acl_obj).split()
for i in dict.keys():
if i in words:
for key in dict[i]:
if words.count('object-group') > 1:
q = 0
while(q<=len(words) - 1): # повторяем пока их не останется 0
if words[q] == 'object-group' and words[q+1] != res: # если каждая итерация = искомой группе и не равна начальной, то выводим результат
otherobj = words[q+1]
for oth1 in parse.find_objects(otherobj):
for cc1 in oth1.children:
print(str(cc1).split("'")[1])
q=q+1
print(acl)Answer the question
In order to leave comments, you need to log in
I don’t know how to do it right
. And I use batfish
to analyze ACL,
and a self-written tool wrapper for the convenience of working with it
, in which I implemented only two functions I need
, proto) through the network or not and thanks to what rule
2. looks for ACEs that will never work
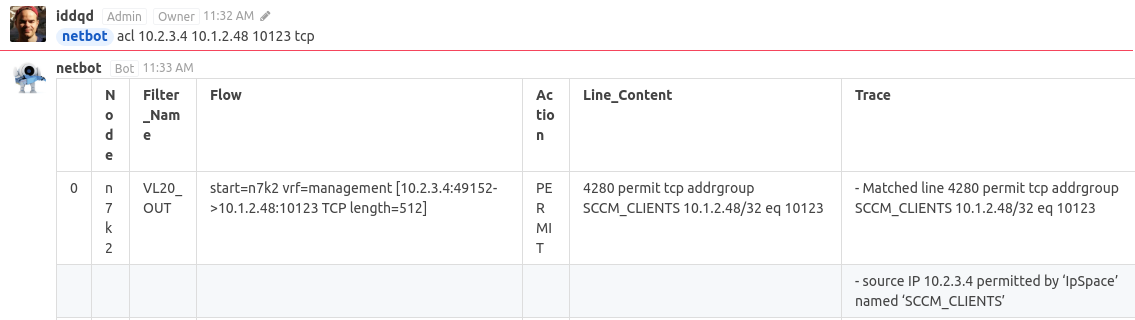
, buttfish can do it himself. It is enough to feed him the device configs and call the necessary functions
. And just checked. ObjectGroups he understands
here is an example:
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question